The Linux server fails to ssh to the platform through the V7 firewall
- 0 Followed
- 0Collected ,1478Browsed
Network Topology
Linux server-SW1-IPSEC-FW-SW2-platform
Problem Description
On-site linux server occasionally has the problem that SSH cannot log in to the platform. When the problem occurs, the server can ssh to the firewall, but when it ssh to SW2 through the firewall, it will prompt that it cannot connect.
Process Analysis
When the problem occurred, it was found that ping was reachable, but ssh login was not possible, so we directly captured the packet and checked it.
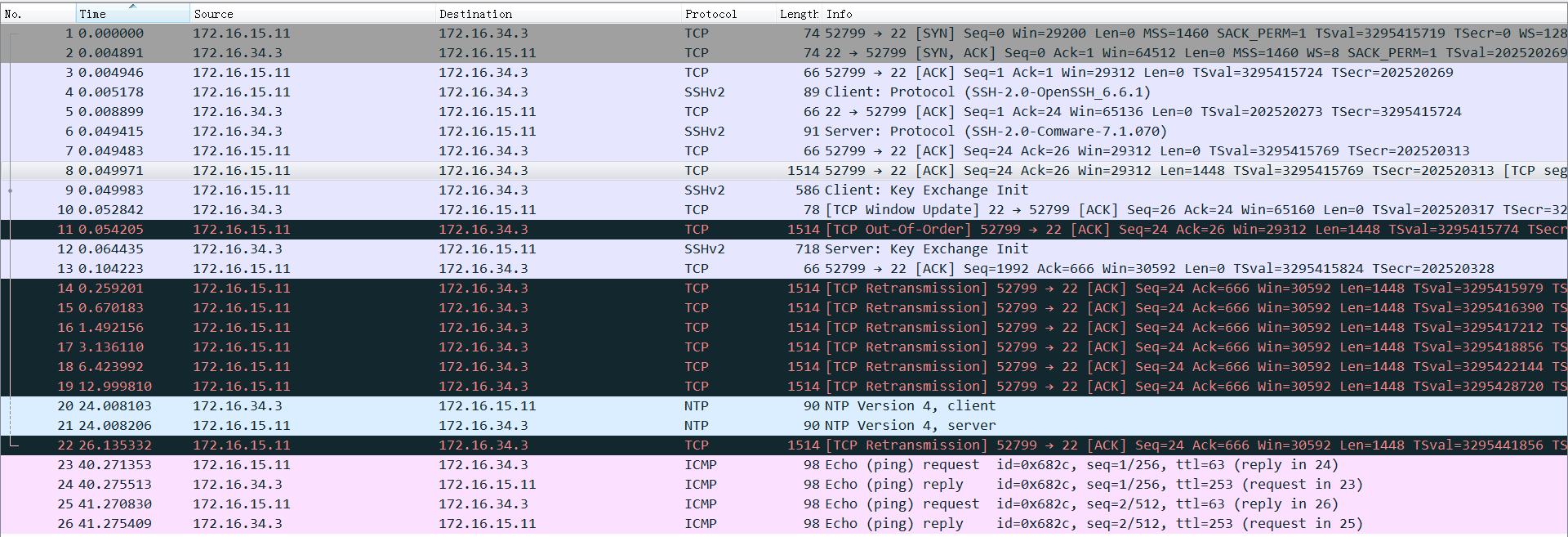
Packets captured on the firewall when ssh fails:
Packets captured on the firewall when ssh succeeds:
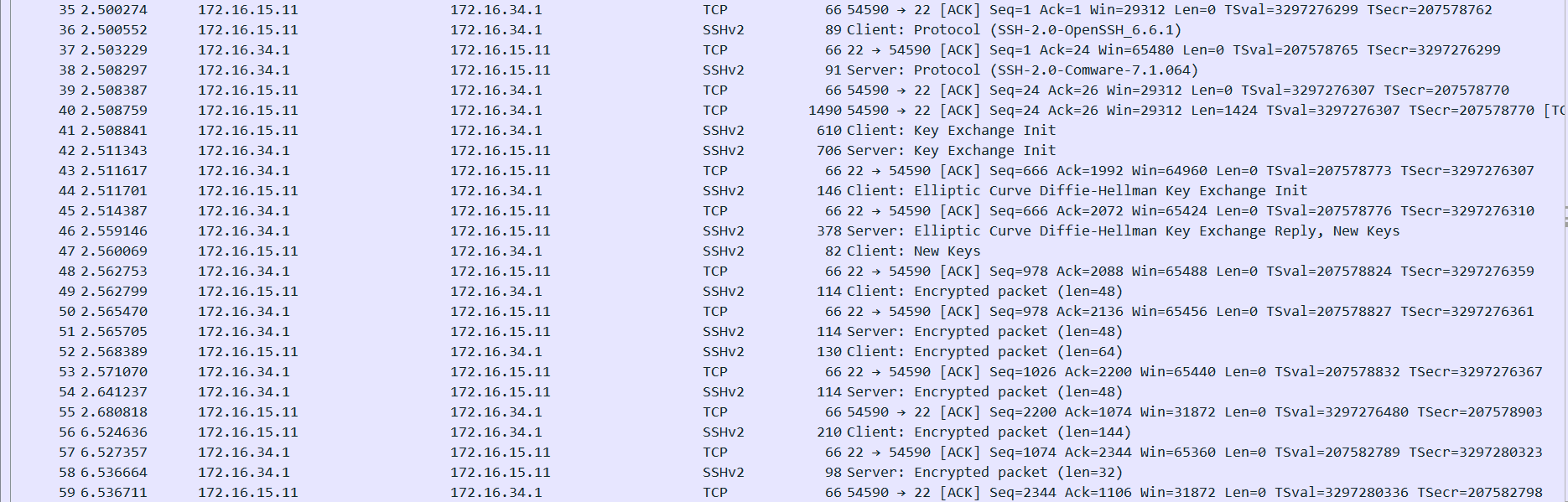
By comparing the captured packets, it can be found that the length of the retransmitted TCP packet when ssh fails is 1514 bytes, and the MTU value of the IPsec tunnel on the firewall is 1444, which is less than 1500.
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Therefore, the problem is located in that the MTU of the IPsec tunnel is less than 1500, which causes large packets to be discarded because they cannot be fragmented and retransmitted.
Solution
Set a smaller internal and external interface tcp mss for the device, so that the segmented packets can smoothly enter the IPsec tunnel for encapsulation.
What is the appropriate TCP setting? Since the IP header and TCP header length of the TCP service message are both 20 bytes, in the IP scenario; TCP MSS = Path MTU – IP Header – TCP Header = Path MTU – 40.
For example, if Path = 1444, then the MSS can be set to 1404 under the internal and external network ports. It does not matter if it is smaller, but it cannot be too small, otherwise TCP packet reassembly will consume a certain amount of performance.