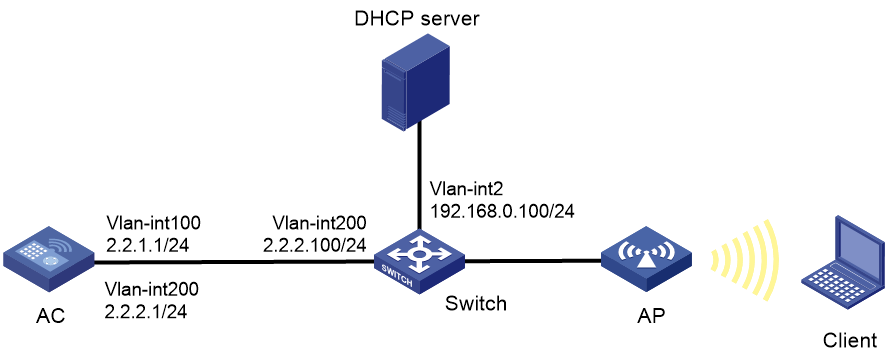
Network Topology
The client can only access the Portal Web server before passing the Portal authentication; after passing the Portal authentication, the client can access the external network.
Problem Description
A guest account is created on the device, but the guest account cannot pass the local portal authentication, and local users can pass the portal authentication.
Process Analysis
1.
#
dhcp server ip-pool pool222
gateway-list 192.168.222.1
network 192.168.222.0 mask 255.255.255.0
dns-list 8.8.8.8
#
wlan service-template service-set1
ssid h3c-ssd-1
user-isolation enable
portal enable method direct
portal domain h3c
portal bas-ip 192.168.1.197
portal apply web-server portal-web
service-template enable
#
wlan service-template service-set2
ssid portal
portal enable method direct
portal domain h3c
portal bas-ip 192.168.1.197
portal apply web-server portal-web
portal ipv4-max-user 654
service-template enable
#
interface Vlan-interface2
ip address 192.168.222.1 255.255.255.0
portal enable method direct
portal domain h3c
portal apply web-server portal-web
#
domain h3c
authentication lan-access radius-scheme radius
authorization lan-access radius-scheme radius
accounting lan-access radius-scheme radius
authentication portal local
authorization portal local
accounting portal local
#
local-user admin class manage
password hash $h$6$22sLW3OhcsSifGOZ$EUXEb8O05CG0Xngdt6AtgbqNKJCin8rKzIhw+xEwYta3p7y96oZlPqI0+8joghtDeaOsbzfpHFo7trWix59/HQ==
service-type telnet http https
authorization-attribute user-role network-admin
#
local-user admin1 class manage
password hash $h$6$lrHM5QpAvrlmMc/3$7m2qD9tAwS9Sd396/Jr3szeyZKVl8u8KUKEKhfd+r217pWW9nnn71gDYKk1FbmM6nSRkUilMSolFFIHrbbPGYA==
service-type ssh telnet http https
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
local-user guest1 class network guest
password cipher $c$3$ttJ2+N/9Z5AMAQwVemF9ze/NexbQG4piiA==
#
local-user guest2 class network guest
password cipher $c$3$/MULrAtGb+lnrG1RDLBhcpYFgiZZ1tRkaQ==
#
local-user guest3 class network guest
password cipher $c$3$q5dSVYgVzM3/BBPEmXiQfJFZAYrmOmFtaw==
full-name guest3
#
local-user h3c class network
password cipher $c$3$zl/9Tf5VcHFRNcrAJzgMBl4X8RB/ng==
service-type portal
authorization-attribute user-role network-operator
#
local-user test1 class network
password cipher $c$3$05jt8K1JXLBjJ8Vqkw68l3AytJ3hvQQx
service-type portal
authorization-attribute user-role network-operator
#
local-user test2 class network
password cipher $c$3$Wpdp9pVn5nbFauluW94fUmbtVmsTjDDJ
service-type portal
authorization-attribute user-role network-operator
#
portal host-check enable
portal free-rule 1 destination ip any udp 53
portal free-rule 1 description 1
#
portal web-server portal-web
url http://192.168.1.197/portal
url-parameter ssid ssid
url-parameter wlanacname value AC
url-parameter wlanuserip source-address
#
portal server s1
ip 192.168.1.60 key cipher $c$3$G/G7KoN/RuOkqXzCsz5kmUAErg6dYOYIWGxYHg==
#
portal local-web-server http
default-logon-page defaultfile_en.zip
#
2.
#
local-user guest3 class network guest
password cipher $c$3$q5dSVYgVzM3/BBPEmXiQfJFZAYrmOmFtaw==
full-name guest3
validity-datetime from 2021/08/18 07:35:00 to 2021/08/20 18:00:00
#
local-user guest4 class network guest
password cipher $c$3$L+svxTEgKos2HLAnmSLWxDem8vFWU7efyg==
full-name guest4
validity-datetime from 2021/09/06 10:48:34 to 2021/09/30 10:48:34
#
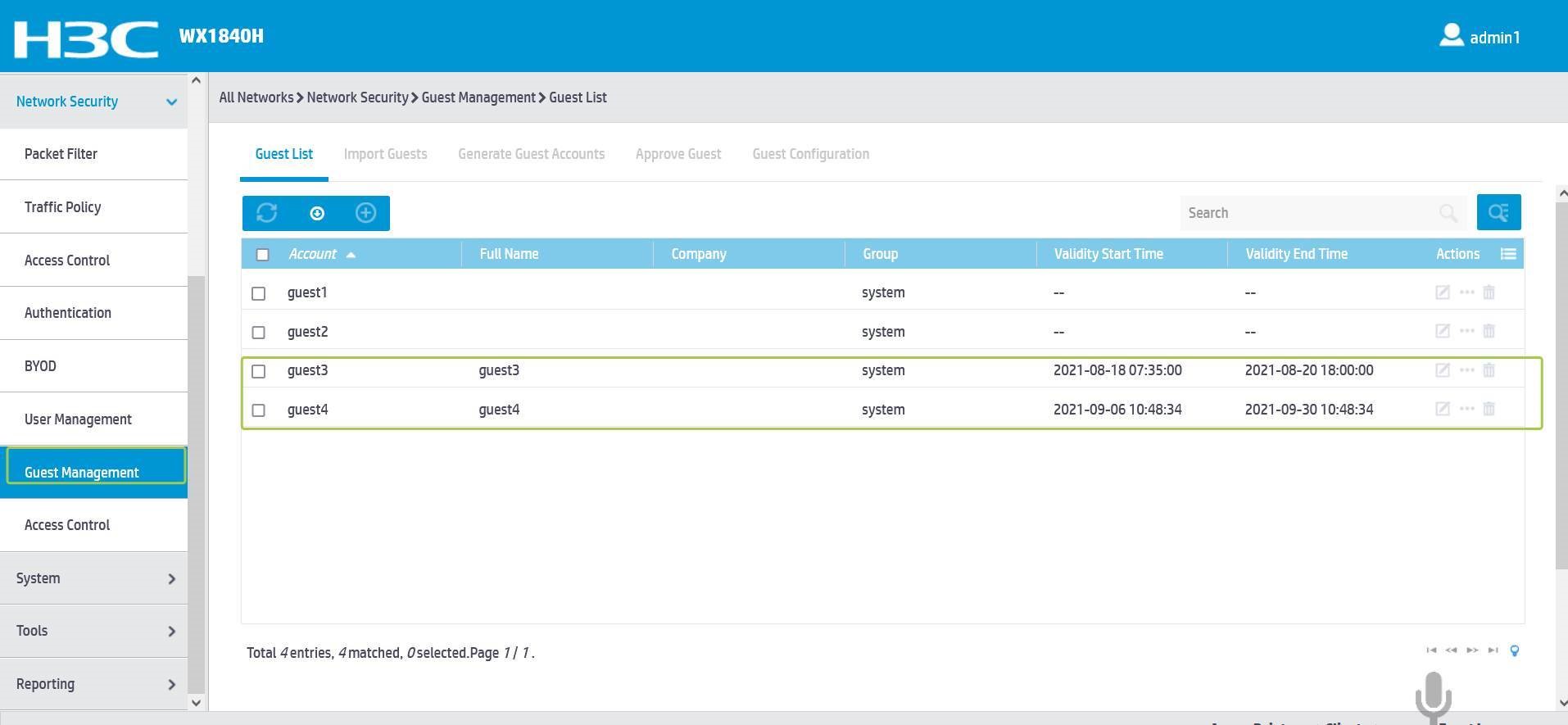
After setting the validity-datetime for the guest user according to the device time, the problem is solved.
Solution
The clock date and NTP configuration were modified, and the problem was solved.
