The web interface prompts not secure when managing the firewall remotely with HTTPS, how to solve it?
- 0 Followed
- 0Collected ,1984Browsed
Network Topology
Not involved
Problem Description
The web interface prompts not secure when managing the firewall remotely with HTTPS, how to solve it?
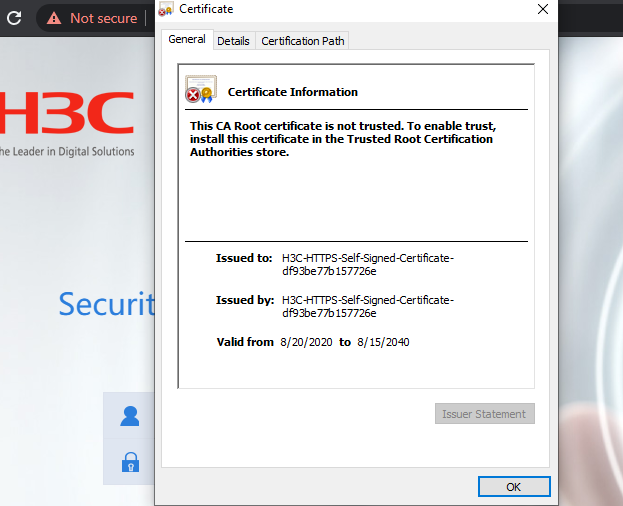
Process Analysis
The device uses a self-signed certificate (a certificate that is generated and signed by the device itself) and the default SSL settings. The device operates in simplified mode after you enable HTTPS service on the device by default.
So it will prompt that it is not secure and you need to import the trusted certificate yourself.
Solution
1. First create a PKI domain:
[H3C] pki domain test
[H3C-pki-domain-test] undo crl check enable
(V5 command: crl check disable)
2. Import CA certificate and local certificate into the PKI domain:
[H3C] pki import domain test der ca filename ca.cer
[H3C] pki import domain test p12 local filename server.pfx
3. Enter the server-side policy view in configuration view with the command ssl server-policy policy-name.
<H3C>system-view
[H3C]ssl server-policy test
4. Refer to the PKI domain.
[H3C-ssl-server-policy-test] pki-domain test
5. Disable the SSL services currently provided to the outside world, such as HTTPS:
[H3C] undo ip https enable
[H3C] undo ip http enable
6. Configure the SSL service such as HTTPS service to refer to the SSL Server side policy customized earlier:
[H3C] ip https ssl-server-policy test
7. Re-enable the SSL service, e.g. re-enable HTTPS service:
[H3C] ip https enable
[H3C] ip http enable
Precautions:
1. the client browser's certificate pair that is ca and local should be chained, to see the certificate status in the certificate detail path is "certificate no problem". The same is true for the device side.
2. the client's ca certificate and the device's ca certificate can be different, but they must trust each other. That is, the client browser should import the ca certificate of the device, and the ca certificate of the client browser should be imported under the pki domain of the device.
3. Normally, you need to configure undo crl check enable under the pki domain of the device.
