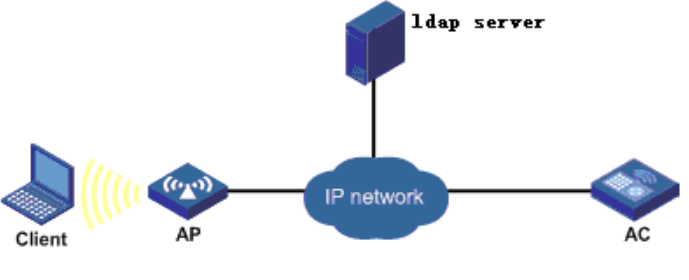
Network Topology
Topology:
Problem Description
How to Implement 802.1X Authentication between Wireless AC Controller and LDAP Server
Process Analysis
There is an LDAP server in the existing network, and the wireless controller needs to be configured to authenticate wireless users. In this scenario, the iNode client needs to be installed to support the PEAP-GTC authentication type.
Solution
1. Device configuration
(1) Import the CA certificate certnew.cer and local certificate server2.pfx into the device through ftp or tftp.
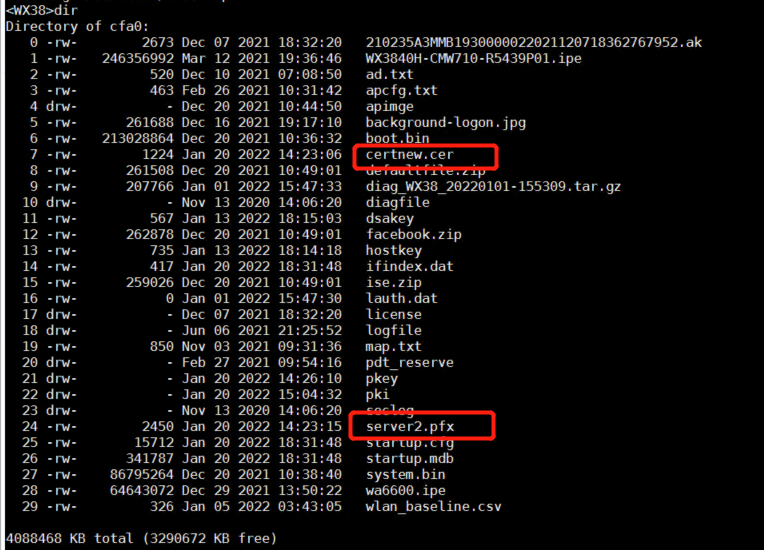
(2) Configure the pki domain and import the certificate.
#Create a PKI domain named test, import the CA certificate certnew.cer and the local certificate server2.pfx.
[WX38]pki domain test
[WX38]pki import domain test pem ca filename certnew.cer
The PKI domain already has a CA certificate. If it is overwritten, local certificates, peer certificates and CRL of this domain will also be deleted.
Overwrite it? [Y/N]:y
The trusted CA's finger print is:
MD5 fingerprint:CEA3 E3EF C7B6 6BFD 8D9E 8174 606C 8D8E
SHA1 fingerprint:4D25 EA37 4885 5E94 3B0E 1B83 7AA7 290D 23A6 4EC3
Is the finger print correct?(Y/N):y
[WX38]pki import domain test p12 local filename server2.pfx
Please input the password:
The device already has a key pair. If you choose to continue, the existing key pair will be overwritten if it is used for the same purpose. The local certificates, if any, will also be overwritten.
Continue? [Y/N]:y
(3) configure ssl server-policy
#Create an SSL server-side policy named ssl-eap, and configure the PKI domain used by the SSL server policy as eap-gtc.
[WX38]ssl server-policy ssl-eap
[WX38-ssl-server-policy-ssl-eap]pki-domain test
(4) Configure the eap-profile template
#Create an EAP authentication scheme named eap-srv, configure the authentication method as PEAP-GTC, and refer to the SSL server-side policy as ssl-eap.
[WX38] eap-profile eap-srv
[WX38-eap-profile-eap-srv] method peap-gtc
[WX38-eap-profile-eap-srv] ssl-server-policy ssl-eap
(5) Configure global dot1x authentication
#Enable the EAP relay mode to support all types of EAP authentication methods between the client and the RADIUS server.
[WX38] dot1x authentication-method eap
(6) Configure ISP template
# Create an ISP domain named eap-gtc and use ldap authentication, none authorization, and none accounting methods.
[WX38] domain ldap
[WX38-isp-local] authentication lan-access ldap-scheme ldap
[WX38-isp-local] authorization lan-access none
[WX38-isp-local] accounting lan-access none
[WX38-isp-local] quit
(5) Configure local ldap
# Create an ldap scheme named ldap and specify the service name.
[WX38] ldap scheme ldap
[WX38-ldap-ldap] authentication-server ldap
[WX38-ldap-ldap] quit
(6) Configure the ldap service configuration
# Create an ldap server named ldap, and specify the user name, password, ldap server IP and access method.
[WX38e] ldap server ldap
[WX38-server-ldap] login-dn cn=administrator,cn=users,dc=overseas,dc=com
[WX38-server-ldap] search-base-dn cn=users,dc=overseas,dc=com
[WX38-server-ldap] ip 172.16.1.110
[WX38-server-ldap] login-password simple 2wsx@WSX
[WX38-server-ldap] quit
(7) Configure the WLAN service template
# Create a service template named 10 and configure the ssid, vlan, authentication method, encryption suite, ISP domain, and eap-profile template.
[WX38] wlan service-template 2
[WX38-wlan-st-10] ssid hwzc
[WX38-wlan-st-10] client forwarding-location ap
[WX38-wlan-st-10] akm mode dot1x
[WX38-wlan-st-10] cipher-suite ccmp
[WX38-wlan-st-10] security-ie rsn
[WX38-wlan-st-10] client-security authentication-mode dot1x
[WX38-wlan-st-10] dot1x domain ldap
[WX38-wlan-st-10] dot1x eap-termination eap-profile eap-srv
[WX38-wlan-st-10] dot1x eap-termination authentication-method pap
[WX38-wlan-st-10] service-template enable
2. iNode customization
#Download the latest version of the iNode software package from the official website
https://www.h3c.com/en/d_202108/1431329_294551_180.htm
After installing iNode Management Center, you need to customize the wireless access function:
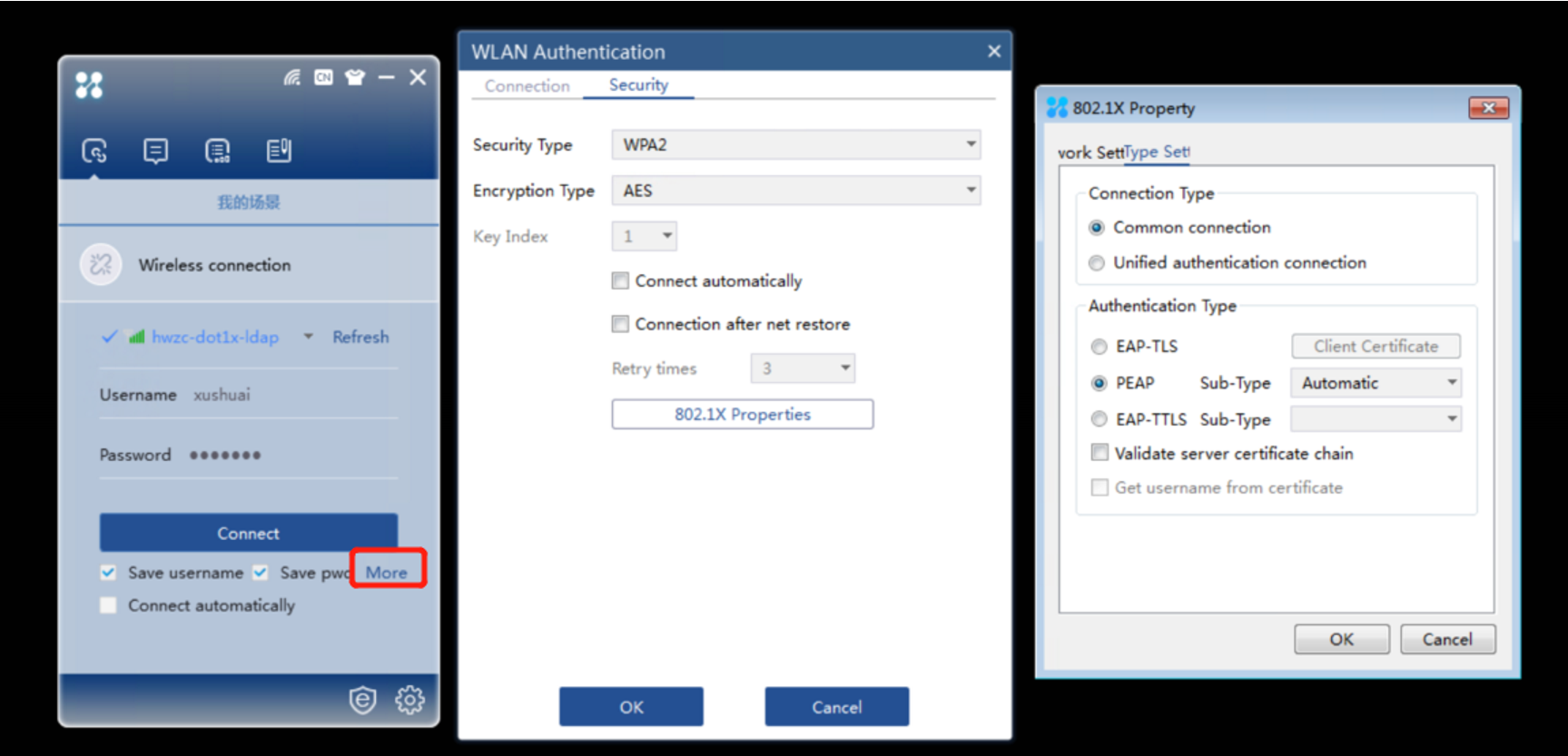
Set the security type WPA2 on the iNode and the encryption method AES. The 802.1X authentication type is EAP-PEAP, and the subtype is automatically gtc:
3. Experimental results
Enter the username and password on the LDAP, click Connect to go online.
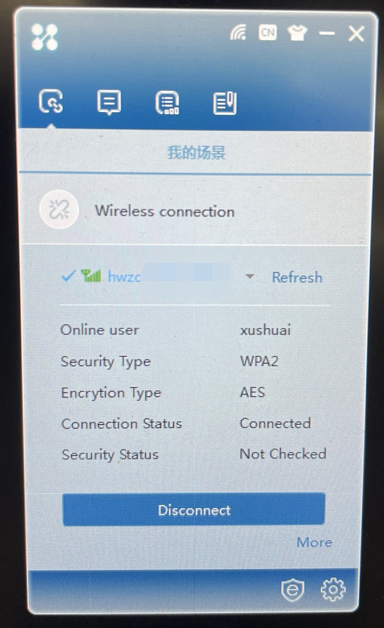
View dot1x authentication results:
<WX38>dis dot1x connection
Total connections: 1
User MAC address : f496-34c5-8b0e
AP name : ap-hwzc
Radio ID : 1
SSID : hwzc
BSSID : f010-903e-b4c1
Username : xushuai
Authentication domain : ldap
IPv4 address : 192.168.100.43
Authentication method : EAP
Initial VLAN : 100
Authorization VLAN : 100
Authorization ACL number : N/A
Authorization user profile : N/A
Authorization CAR : N/A
Authorization URL : N/A
Authorization IPv6 URL : N/A
Termination action : N/A
Session timeout last from : N/A
Session timeout period : N/A
Online from : 2022/01/20 14:29:54
Online duration : 0h 14m 6s
View LDAP related information:
<WX38>dis ldap scheme
Total 1 LDAP schemes
------------------------------------------------------------------
LDAP scheme name : ldap
Authentication server : ldap
IP : 172.16.1.110
Port : 389
VPN instance : Not configured
LDAP protocol version : LDAPv3
Server timeout interval : 10 seconds
Login account DN : cn=administrator,cn=users,dc=overseas,dc=com
Base DN : cn=users,dc=overseas,dc=com
Search scope : all-level
User searching parameters:
User object class : Not configured
Username attribute : cn
Username format : without-domain
Group filter : (objectclass=group)
Authorization server : Not configured
Attribute map : Not configured
