Use ACL to realize that different SSIDs can only access specific terminals and access specific traffic
- 0 Followed
- 0Collected ,1500Browsed
Network Topology
Topology
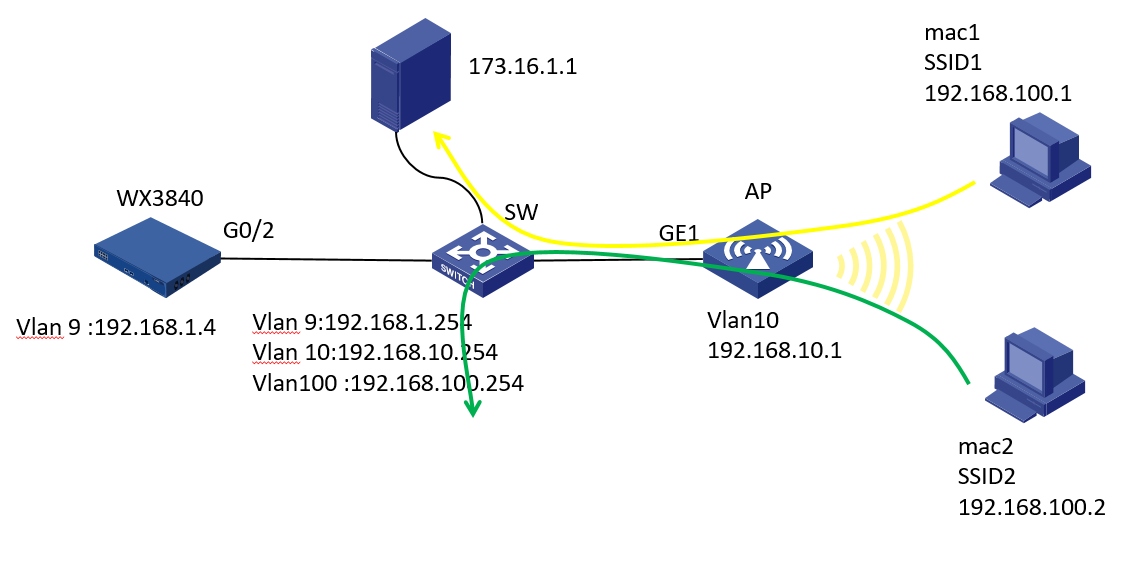
Problem Description
Customer site requirements: The terminal under a specific SSID in the wireless network planning can only access the server on the internal network, and other SSIDs can access the external network
Process Analysis
All terminals on site are in one network segment.
Use mac local authentication and user group to realize that the terminal under SSID1 can only access the intranet server, and use the packet filter under the service template to realize that the terminal under other SSID2 cannot access the intranet server
Solution
# Create acl 3000 include the intranet server server IP
[AC]acl advanced 3000
[AC]rule 0 permit ip destination 173.16.1.1 0
[AC]rule 5 permit ip source 173.16.1.1 0
#Add user group authorization ACL3000
[AC]user-group mac-local
[AC]authorization-attribute acl 3000
#Add some specific users' mac accounts and join user groups
[AC]local-user 08c729d861f2 class network
[AC]password cipher $c$3$Iy9rPXZMqvcLYPlrbXY6sUzV2uTLfB/ryCD4Gpi3bw==
[AC]service-type lan-access
[AC]group mac-local
[AC]authorization-attribute user-role network-operator
#
[AC]domain mac-local
[AC]authorization-attribute idle-cut 15 1024
[AC]authentication lan-access local
[AC]authorization lan-access none
[AC]accounting lan-access none
#Enable mac authentication under service template SSID1
[AC]wlan service-template 1
[AC]ssid hwzc-mac-local-authoriztion
[AC]client forwarding-location ap
[AC]client-security authentication-mode mac
[AC]mac-authentication domain mac-local
[AC]service-template enable
#Configure the user's MAC address as the username and password, using the MAC address format without the hyphen "-", where the letters are capitalized
[AC]mac-authentication user-name-format mac-address without-hyphen lowercase
#AC are configured with ACL3010 to deny access to the destination address
[AC]acl advanced 3010
[AC]rule 0 deny ip source 173.16.1.1 0
[AC]rule 5 deny ip destination 173.16.1.1 0
#The service template calls packet-filter acl 3010 and restarts the service template
[AC]wlan service-template 2
[AC]ssid hwzc-dot1x-imc
[AC]client forwarding-location ap
[AC]packet-filter 3010 inbound
[AC]packet-filter 3010 outbound
[AC]akm mode dot1x
[AC]cipher-suite ccmp
[AC]security-ie rsn
[AC]client-security authentication-mode dot1x
[AC]dot1x domain imc-dot1x
[AC]service-template enable
--------------------------------------------------------------------------
#APs are configured with ACL3010 to deny access to the destination address
[AP]acl advanced 3010
[AP]rule 0 deny ip source 173.16.1.1 0
[AP]rule 5 deny ip destination 173.16.1.1 0
