Network Topology
The client has two ISP addresses, two SSL VPN contexts are configured, and remote clients can dial into the SSL VPN through both ISP addresses.
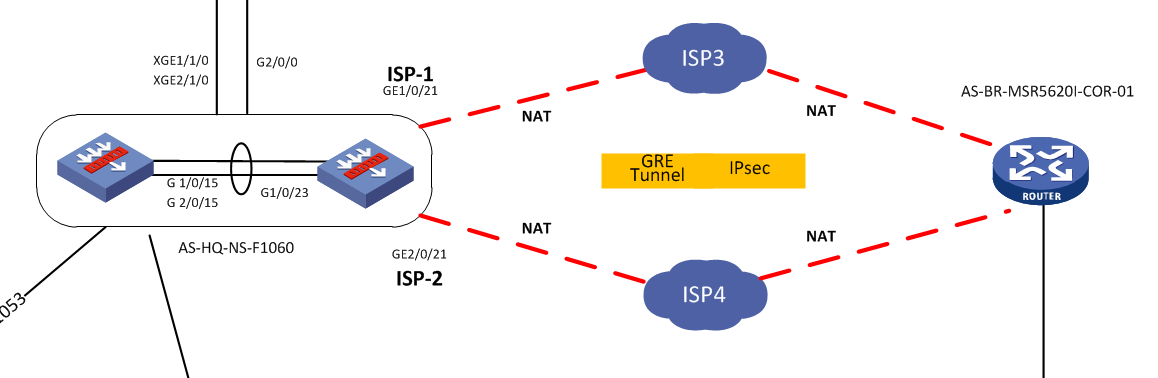
Problem Description
The remote client dials in to sslvpn through the two ISP addresses on the F1060. The two ISP addresses are on the two slots respectively, and the firewall does an IRF. Because SSL VPN traffic can only be encrypted and decrypted in the master slot, after decryption, the routing priority will be directly forwarded from the master slot, resulting in inconsistent round-trip VPN traffic, and accounts dialed in through ISP 2 cannot access intranet resources normally.
Process Analysis
In order to ensure that the traffic entering the firewall from slot 2 is forwarded from slot 2 and is not affected by routing, we adopt the method of dividing VPN instances and bind the two VPN services to the two VRFs. Therefore, different VPNs cannot communicate with each other. Each VRF maintains an independent routing table to ensure that VPN traffic is forwarded in the same slot.
Solution
#
ip vpn-instance sslvpn1
#
ip vpn-instance sslvpn2
#
interface Ten-GigabitEthernet1/1/0.50
ip binding vpn-instance sslvpn1
ip address 10.50.50.1 255.255.255.252
vlan-type dot1q vid 50
#
interface Ten-GigabitEthernet2/1/0.50
ip binding vpn-instance sslvpn2
ip address 10.51.51.1 255.255.255.0
vlan-type dot1q vid 51
#
interface SSLVPN-AC1
mtu 1800
ip binding vpn-instance sslvpn1
ip address 10.100.10.1 255.255.255.0
#
interface SSLVPN-AC2
mtu 1800
ip binding vpn-instance sslvpn2
ip address 10.100.20.1 255.255.255.0
#
security-zone name Trust
import interface SSLVPN-AC1
import interface SSLVPN-AC2
import interface Ten-GigabitEthernet1/1/0.50
import interface Ten-GigabitEthernet2/1/0.50
#
ip route-static vpn-instance sslvpn1 10.0.0.0 8 10.50.50.2
ip route-static vpn-instance sslvpn1 10.26.10.0 24 10.50.50.2
ip route-static vpn-instance sslvpn1 10.30.10.0 24 10.50.50.2
ip route-static vpn-instance sslvpn1 10.100.10.0 24 10.50.50.2
ip route-static vpn-instance sslvpn1 172.16.0.0 24 10.50.50.2
ip route-static vpn-instance sslvpn1 172.16.10.0 24 10.50.50.2
ip route-static vpn-instance sslvpn1 192.168.0.0 24 10.50.50.2
ip route-static vpn-instance sslvpn1 192.168.10.0 24 10.50.50.2
ip route-static vpn-instance sslvpn2 10.0.0.0 8 10.51.51.2
ip route-static vpn-instance sslvpn2 10.20.10.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 10.26.10.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 10.30.10.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 10.100.10.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 172.16.0.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 172.16.10.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 192.168.0.0 24 10.51.51.2
ip route-static vpn-instance sslvpn2 192.168.10.214 32 10.51.51.2
ip route-static vpn-instance sslvpn2 192.168.10.215 32 10.51.51.2
#
sslvpn ip address-pool sslvpnpool 10.100.10.2 10.100.10.100
sslvpn ip address-pool sslvpnpool2 10.100.20.10 10.100.20.50
#
sslvpn gateway gw
ip address 1.1.1.1 port 4430
service enable
#
sslvpn gateway gw1
ip address 2.2.2.2 port 4430
service enable
#
sslvpn context ctx2ip
vpn-instance sslvpn2
gateway gw1
ip-tunnel interface SSLVPN-AC2
ip-tunnel address-pool sslvpnpool2 mask 255.255.255.0
ip-tunnel log connection-close
ip-tunnel log packet-drop
ip-tunnel log address-alloc-release
logo file download.png
ip-route-list external
include 10.26.10.0 255.255.255.0
include 10.30.10.0 255.255.255.0
include 10.100.10.0 255.255.255.0
include 172.16.0.0 255.255.255.0
include 172.16.10.0 255.255.255.0
include 192.168.0.0 255.255.255.0
ip-route-list rtlist
include 10.0.0.0 255.0.0.0
include 10.20.10.0 255.255.255.0
include 10.26.10.0 255.255.255.0
include 192.168.0.0 255.255.255.0
include 192.168.10.214 255.255.255.255
include 192.168.10.215 255.255.255.255
policy-group external
filter ip-tunnel acl 3995
ip-tunnel access-route ip-route-list external
policy-group resourcegrp
filter ip-tunnel acl 3994
ip-tunnel access-route ip-route-list rtlist
default-policy-group resourcegrp
log user-login enable
log resource-access enable filtering brief
service enable
#
sslvpn context ctxip
vpn-instance sslvpn1
gateway gw
ip-tunnel interface SSLVPN-AC1
ip-tunnel address-pool sslvpnpool mask 255.255.255.0
ip-tunnel log connection-close
ip-tunnel log packet-drop
ip-tunnel log address-alloc-release
logo file download.png
uri-acl external
ip-route-list external
include 10.26.10.0 255.255.255.0
include 10.30.10.0 255.255.255.0
include 10.100.10.0 255.255.255.0
include 172.16.0.0 255.255.255.0
include 172.16.10.0 255.255.255.0
include 192.168.0.0 255.255.255.0
ip-route-list rtlist
include 10.0.0.0 255.0.0.0
include 10.26.10.0 255.255.255.0
include 192.168.0.0 255.255.255.0
include 192.168.10.0 255.255.255.0
policy-group external
filter ip-tunnel acl 3013
ip-tunnel access-route ip-route-list external
policy-group resourcegrp
filter ip-tunnel acl 3003
ip-tunnel access-route ip-route-list rtlist
default-policy-group resourcegrp
log user-login enable
log resource-access enable filtering brief
service enable
#
security-policy ip
rule 41 name VPN2-pass
action pass
vrf sslvpn2
rule 40 name VPN-pass
action pass
vrf sslvpn1
#
Note: The context, AC port, and intranet resources need to be in the same VRF, and the security policy of action pass needs to be configured.
