Multi subnet VPN ipsec
- 0 Followed
- 0Collected ,1781Browsed
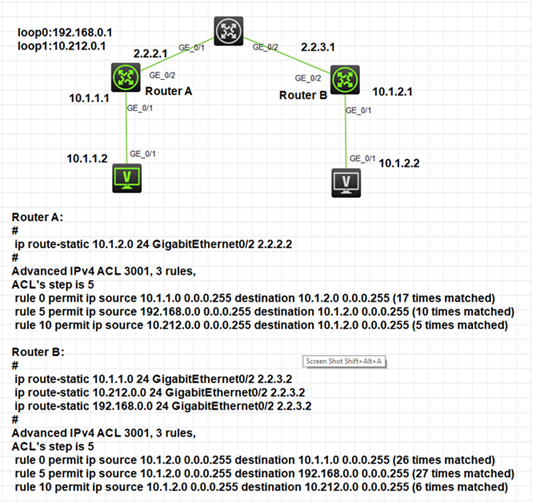
Network Topology
Configuration Steps
Route A:
#
sysname Route A
#
ospf 1
area 0.0.0.0
network 2.2.2.0 0.0.0.255
#
#
interface LoopBack0
ip address 192.168.0.1 255.255.255.0
#
interface LoopBack1
ip address 10.212.0.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
description mgt
combo enable copper
ip address 1.1.1.1 255.255.255.0
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet0/2
port link-mode route
combo enable copper
ip address 2.2.2.1 255.255.255.0
ipsec apply policy map1
#
ip route-static 10.1.2.0 24 GigabitEthernet0/2 2.2.2.2
#
ssh server enable
#
acl advanced 3001
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 10 permit ip source 10.212.0.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
#
#
ipsec transform-set tran1
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy map1 10 isakmp
transform-set tran1
security acl 3001
local-address 2.2.2.1
remote-address 2.2.3.1
ike-profile profile1
#
ike profile profile1
keychain keychain1
match remote identity address 2.2.3.1 255.255.255.0
#
ike keychain keychain1
pre-shared-key address 2.2.3.1 255.255.255.0 key cipher $c$3$xWK8Ib7X6RlFZLR5I7w6I4+n1k4GmOyrvac=
#
Router B:
#
sysname Router B
#
ospf 1
area 0.0.0.0
network 2.2.3.0 0.0.0.255
#
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 1.1.1.2 255.255.255.0
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.1.2.1 255.255.255.0
#
interface GigabitEthernet0/2
port link-mode route
combo enable copper
ip address 2.2.3.1 255.255.255.0
ipsec apply policy use1
#
ip route-static 10.1.1.0 24 GigabitEthernet0/2 2.2.3.2
ip route-static 10.212.0.0 24 GigabitEthernet0/2 2.2.3.2
ip route-static 192.168.0.0 24 GigabitEthernet0/2 2.2.3.2
#
ssh server enable
#
acl advanced 3001
rule 0 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
rule 10 permit ip source 10.1.2.0 0.0.0.255 destination 10.212.0.0 0.0.0.255
#
#
ipsec transform-set tran1
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy use1 10 isakmp
transform-set tran1
security acl 3001
local-address 2.2.3.1
remote-address 2.2.2.1
ike-profile profile1
#
ike profile profile1
keychain keychain1
match remote identity address 2.2.2.1 255.255.255.0
#
ike keychain keychain1
pre-shared-key address 2.2.2.1 255.255.255.0 key cipher $c$3$nxyHBQ4HMibTN08upK14ai7wz55vfO8aM1s=
#
////verification result:
-------------------------------
Interface: GigabitEthernet0/2
-------------------------------
-----------------------------
IPsec policy: map1
Sequence number: 10
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1428
Tunnel:
local address: 2.2.2.1
remote address: 2.2.3.1
Flow:
sour addr: 10.1.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3867484883 (0xe68522d3)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/2977
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 1150524503 (0x44939c57)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/2977
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: N
Status: Active
-----------------------------
IPsec policy: map1
Sequence number: 10
Mode: ISAKMP
-----------------------------
Tunnel id: 1
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1428
Tunnel:
local address: 2.2.2.1
remote address: 2.2.3.1
Flow:
sour addr: 192.168.0.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1056131476 (0x3ef34994)
Connection ID: 4294967298
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3001
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 1381768642 (0x525c1dc2)
Connection ID: 4294967299
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3001
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: N
Status: Active
-----------------------------
IPsec policy: map1
Sequence number: 10
Mode: ISAKMP
-----------------------------
Tunnel id: 2
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1428
Tunnel:
local address: 2.2.2.1
remote address: 2.2.3.1
Flow:
sour addr: 10.212.0.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 890041887 (0x350cf61f)
Connection ID: 4294967300
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3031
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 228441179 (0x0d9dbc5b)
Connection ID: 4294967301
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3031
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: N
Status: Active
Key Configuration
acl & router-static
