PXE pre-boot firmware installation issue
- 0 Followed
- 0Collected ,1942Browsed
Network Topology
PXE client directlty connected to the switch H3C 5560.
Problem Description
We faced with problem regarding pre-boot firmware instalation with PXE. On the vlan-interface of the switch we configured dhcp rely agent. There is no problem with accessibility to dhcp server. All necessary information regarding PXE is configured on the DHCP server (options 67, 60). However PXE client can not to download/install programs throught that switch. But, we reproduced the same connection scheme through the cisco or huawei switch, everything worked without problems.
Process Analysis
From the analysis of the captured packets, the device has successfully requested the Boot file name: smsboot\x64\wdsmgfw.efi file twice, but the program requested to be downloaded later has not been acked. So I compared the two DHCP request messages and found that their option fields are somewhat different.
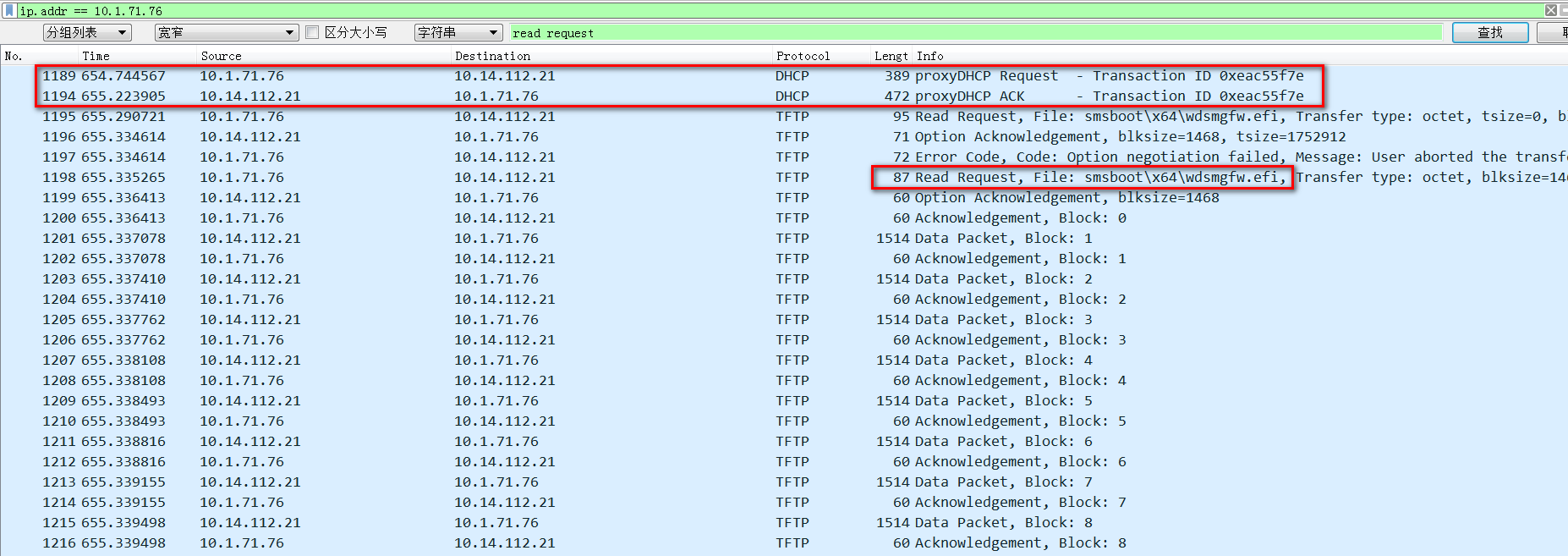
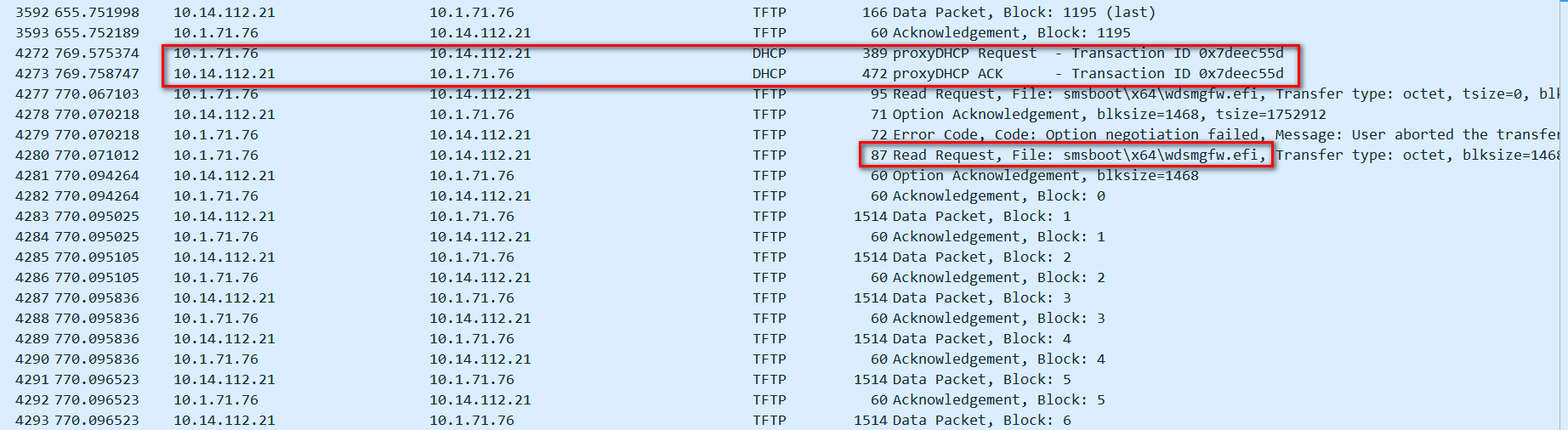
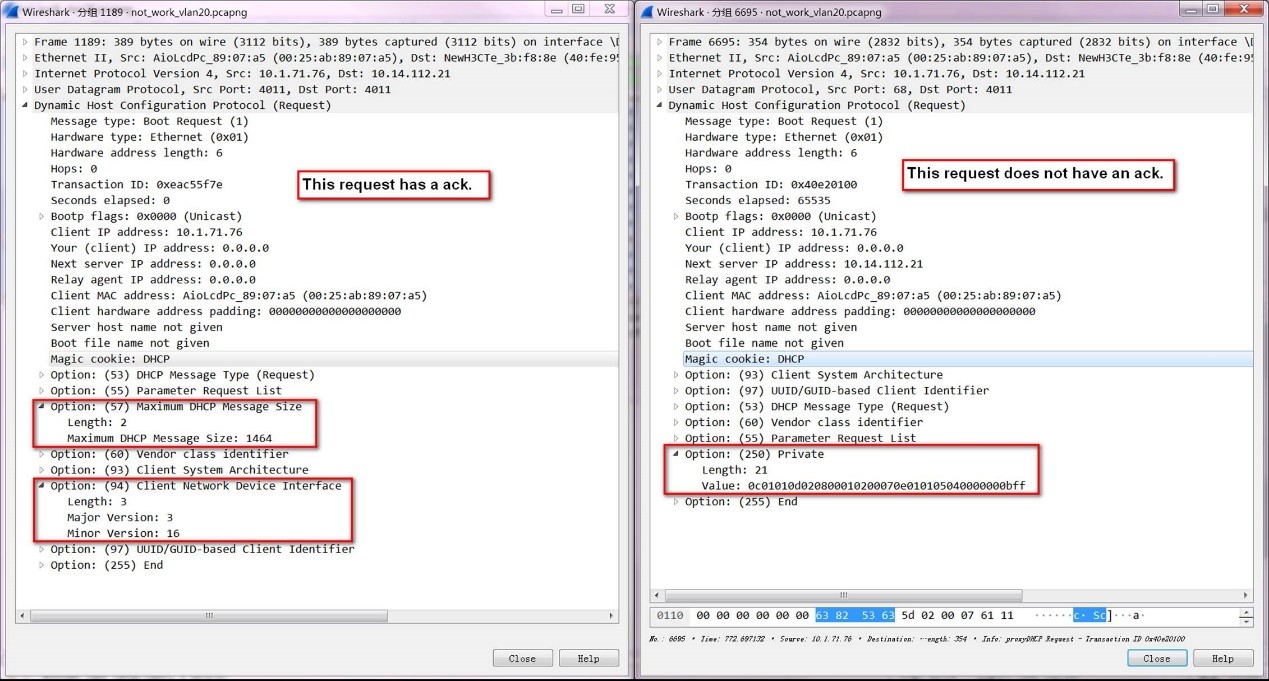
On the Cisco switch, the normal packet capture is as follows, that is to say, the proxyDHCP Request packet requested for the second download is the same, but there is no proxyDHCP ACK packet when it passes through our device. Comparing the two ACK messages, we find that the destination port and source port of the first ACK are both 4011, while the destination port of the second ACK is 68.
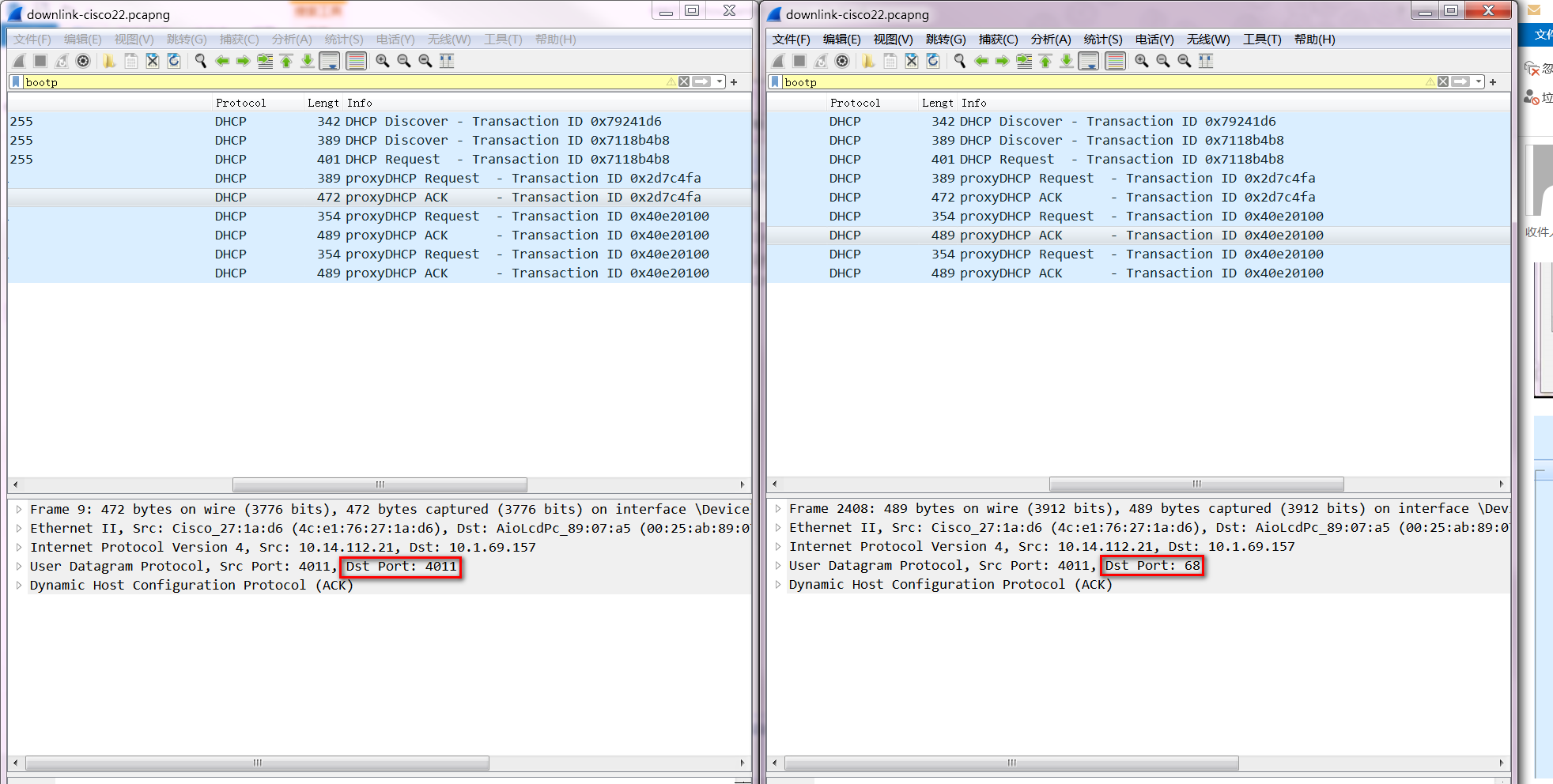
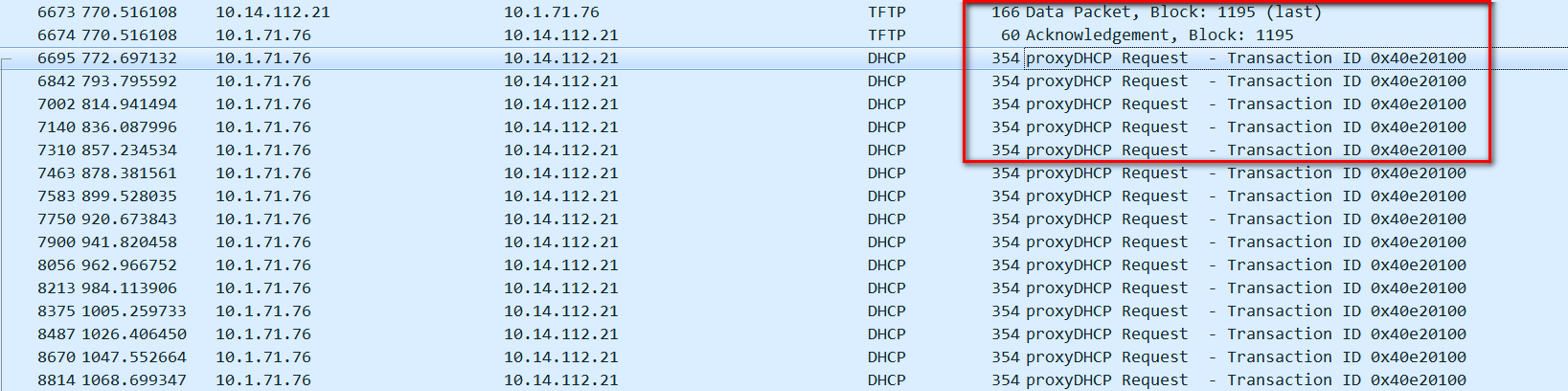
After replaying packets in the laboratory, R&D found that if the device has dhcp snooping enabled and the port is not in the trusted port list, the device will discard the ACK packet.
Check the snooping trusted port and find that the port that the device connects to the server is not listed below:
[GW86-kbl-fl4-h3c]dis dhcp snooping trust
DHCP snooping is enabled.
Interface Trusted VLAN
============================ ======= ================
BAGG2 Trusted -
XGE1/0/51 Trusted -
VSI name Tunnel trusted
============================ ============
AC Trusted
=================================== ============
Solution
Configure dhcp snooping trust on the uplink port.
Attach a detailed explanation of dhcp snooping:
About DHCP snooping
DHCP snooping is a security feature for DHCP.
DHCP snooping works between the DHCP client and server, or between the DHCP client and DHCP relay agent. It guarantees that DHCP clients obtain IP addresses from authorized DHCP servers. Also, it records IP-to-MAC bindings of DHCP clients (called DHCP snooping entries) for security purposes.
DHCP snooping defines trusted and untrusted ports to make sure clients obtain IP addresses only from authorized DHCP servers.
· Trusted—A trusted port can forward DHCP messages correctly to make sure the clients get IP addresses from authorized DHCP servers.
· Untrusted—An untrusted port discards received DHCP-ACK and DHCP-OFFER messages to prevent unauthorized servers from assigning IP addresses.
