F1000 and Huawei USG6620 to configure ikev2 IPsec VPN case
- 0 Followed
- 0Collected ,2721Browsed
Network Topology
Network Topology:
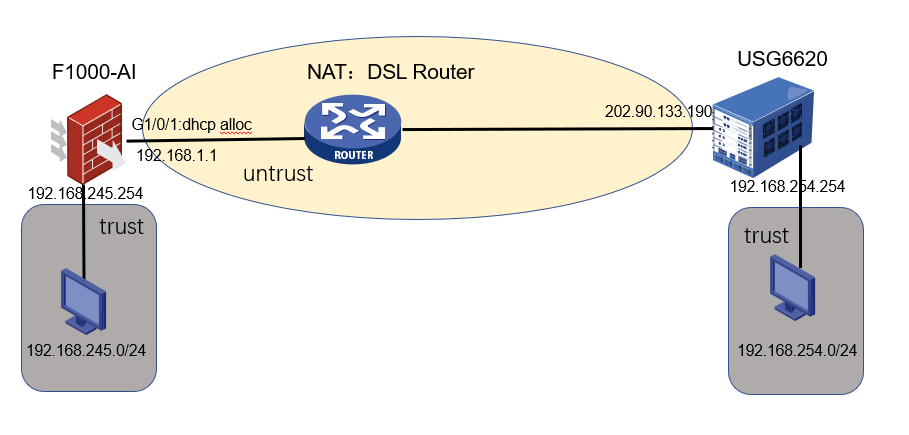
Problem Description
The customer headquarters uses Huawei USG6620 firewall devices, and the branch uses H3C F1000 firewalls. An ipsec tunnel is established between the headquarters and the branch.
Process Analysis
How to complete the ipsec vpn configuration with huawei firewall device.
1.The ipsec of the firewall equipment in the headquarters uses IKEv2 to establish an IPsec tunnel to protect IPv4 packets. Therefore, the branch equipment needs to use IKEv2 to establish an IPsec tunnel synchronously.
2.The egress IP address of the branch firewall F1000 is dynamically obtained by dhcp, and the IP address is not fixed. Therefore, the branch device needs to use the local identity of the FQDN (Fully Qualified Domain Name) type.
3.In order to avoid the ipsec interest flow being converted by nat, it is necessary to remove the ipsec interest flow in the rule of NAT ACL.
Solution
F1000-AI branch configuration:
acl advanced 3000
rule 0 permit ip source 192.168.245.0 0.0.0.255 destination 192.168.244.0 0.0.0.255
rule 1 permit ip source 192.168.245.0 0.0.0.255 destination 192.168.247.0 0.0.0.255
rule 2 permit ip source 192.168.245.0 0.0.0.255 destination 192.168.248.0 0.0.0.255
rule 3 permit ip source 192.168.245.0 0.0.0.255 destination 192.168.249.0 0.0.0.255
rule 4 permit ip source 192.168.245.0 0.0.0.255 destination 192.168.250.0 0.0.0.255
#
acl advanced name A333
rule 0 deny ip source 192.168.245.0 0.0.0.255 destination 192.168.244.0 0.0.0.255
rule 1 deny ip source 192.168.245.0 0.0.0.255 destination 192.168.247.0 0.0.0.255
rule 2 deny ip source 192.168.245.0 0.0.0.255 destination 192.168.248.0 0.0.0.255
rule 3 deny ip source 192.168.245.0 0.0.0.255 destination 192.168.249.0 0.0.0.255
rule 4 deny ip source 192.168.245.0 0.0.0.255 destination 192.168.250.0 0.0.0.255
rule 5 permit ip
#
ipsec transform-set transform1
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
#
ipsec policy policy1 1 isakmp
transform-set transform1
security acl 3000
remote-address 202.90.133.190
ikev2-profile profile2
#
ike identity fqdn butuan
ike logging negotiation enable
#
ikev2 keychain keychain2
peer huawei
address 202.90.133.190 255.255.255.248
identity address 202.90.133.190
pre-shared-key ciphertext $c$3$3QGafg1zi9T1ABwXt+vcu/ygYgJk1wkRPViGrC8CrFQ=
#
ikev2 profile profile2
authentication-method local pre-share
authentication-method remote pre-share
keychain keychain2
identity local fqdn butuan
match remote identity address 202.90.133.190 255.255.255.248
#
ikev2 proposal 2
encryption aes-cbc-256
integrity sha256
dh group14
prf sha256
#
interface GigabitEthernet1/0/1
port link-mode route
description GuideWan Interface
ip address dhcp-alloc
dns server 8.8.4.4
dns server 8.8.8.8
nat outbound name A333
manage http inbound
manage http outbound
manage https inbound
manage https outbound
manage ping inbound
manage ping outbound
manage snmp inbound
manage ssh inbound
manage ssh outbound
manage telnet inbound
manage telnet outbound
ipsec apply policy policy1
#
Huawei USG6620 headquarters configuration:
acl number 3000
rule 660 permit ip source address-set NHQ(LAN) destination address-set "BJMP RO3 LAN"
rule 665 permit ip source address-set NHQ(LAN) destination address-set "BJMP NCRO LAN"
rule 670 permit ip source address-set NHQ(LAN) destination address-set "BJMP RO4A LAN"
rule 675 permit ip source address-set NHQ(LAN) destination address-set "BJMP RO4B LAN"
rule 730 permit ip source address-set NHQ(LAN) destination address-set "BJMP RO6 LAN"
rule 805 permit ip source address-set "JSIOC Network" destination address-set "ALL RO"
rule 810 permit ip source address-set "ALL RO" destination address-set "JSIOC Network"
rule 830 permit ip source address-set NHQ(LAN) destination address-set "JSIOC Network"
rule 835 permit ip source address-set "JSIOC Network" destination address-set NHQ(LAN)
rule 840 permit ip source address-set "JSIOC Network" destination address-set "JSIOC Network"
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer ike69154846815
exchange-mode auto
pre-shared-key %^%#xW"<"6RdWHdq}"P}m;^P}ZNW2C;>+D)=>|:L+;xP%^%#
ike-proposal 1
local-id 202.90.133.190
rsa encryption-padding pkcs1
rsa signature-padding pkcs1
ike negotiate compatible
local-id-preference certificate enable
ikev2 authentication sign-hash sha1
#
ipsec proposal prop69154846816
encapsulation-mode auto
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ipsec policy-template tpl69154846816 1
security acl 3000
ike-peer ike69154846815
proposal prop69154846816
tunnel local 202.90.133.190
alias JU&RO to NHQ
sa duration traffic-based 20971520
sa duration time-based 3600
#
ipsec policy ipsec6915484693 10000 isakmp template tpl69154846816
#
interface GigabitEthernet1/0/9
undo shutdown
ip address 202.90.133.190 255.255.255.248
alias IGOV Internet
healthcheck GDNS
gateway 202.90.133.185
service-manage https permit
service-manage ping permit
service-manage ssh permit
bandwidth ingress 800000 threshold 95
bandwidth egress 800000 threshold 95
ipsec policy ipsec6915484693
#
IPsec vpn connection result:
Ping 192.168.250.254 (192.168.250.254) from 192.168.245.254: 56 data bytes, press CTRL+C to break
56 bytes from 192.168.250.254: icmp_seq=0 ttl=255 time=39.550 ms
56 bytes from 192.168.250.254: icmp_seq=1 ttl=255 time=30.418 ms
56 bytes from 192.168.250.254: icmp_seq=2 ttl=255 time=93.727 ms
56 bytes from 192.168.250.254: icmp_seq=3 ttl=255 time=32.529 ms
56 bytes from 192.168.250.254: icmp_seq=4 ttl=255 time=30.849 ms
--- Ping statistics for 192.168.250.254 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
-----------------------------------------------------------------
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
2 192.168.1.1/4500 202.90.133.190/4500 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
-------------------------------
Interface: GigabitEthernet1/0/1
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Initiator
Path MTU: 1416
Tunnel:
local address: 192.168.1.1
remote address: 202.90.133.190
Flow:
sour addr: 192.168.245.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.168.250.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1231797916 (0x496bbe9c)
Connection ID: 12502649798656
Transform set: ESP-ENCRYPT-AES-CBC-256 ESP-AUTH-SHA256
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3416
Max received sequence-number: 10
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 200538556 (0x0bf3f9bc)
Connection ID: 2005749727233
Transform set: ESP-ENCRYPT-AES-CBC-256 ESP-AUTH-SHA256
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3416
Max sent sequence-number: 9
UDP encapsulation used for NAT traversal: Y
Status: Active
