Network Topology
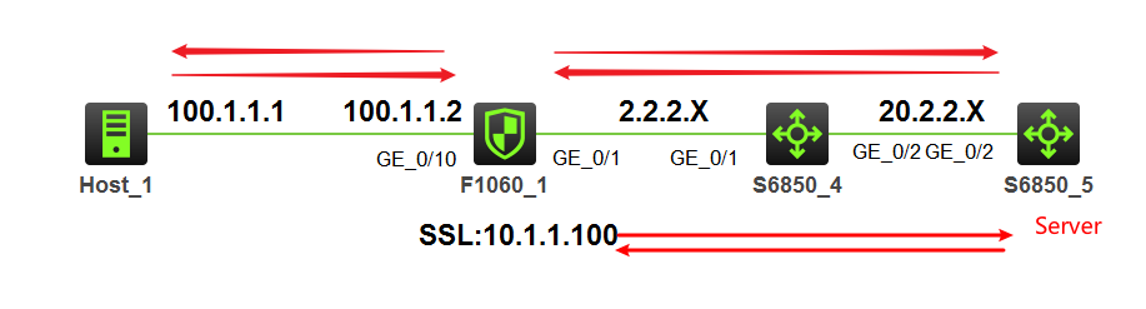 as above
as above
Configuration Steps
1. Check basic SSL VPN configuration.
interface GigabitEthernet0/1
port link-mode route
ip address 100.1.1.2 255.255.255.0 ----Public Interface IP address
#
interface GigabitEthernet0/2
port link-mode route
ip address 2.2.2.2 255.255.255.0 ----LAN Interface IP address
#
interface SSLVPN-AC1
ip address 10.1.1.100 255.255.255.0 ----SSL-AC Interface IP address
#
acl advanced 3000
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 2.2.2.0 0.0.0.255 ----ACL from SSL client to LAN network
#
local-user sslvpnuser class network ----SSLVPN Local User
password simple 123456
authorization-attribute user-role network-operator
authorization-attribute sslvpn-policy-group resourcegrp
#
sslvpn ip address-pool sslvpnpool 10.1.1.1 10.1.1.10 ----SSLVPN IP Pool
#
sslvpn gateway gw ----SSLVPN gateway
ip address 100.1.1.2 port 4430
service enable
#
sslvpn context ctxip ----SSLVPN context
gateway gw
ip-tunnel interface SSLVPN-AC1
ip-tunnel address-pool sslvpnpool mask 255.255.255.0
ip-route-list rtlist
include 2.2.2.0 255.255.255.0
policy-group resourcegrp
filter ip-tunnel acl 3000
ip-tunnel access-route ip-route-list rtlist
service enable
#
return
2.Check security-zone configuration:
security-zone name untrust
import interface fw-wan
import interface sslvpn-ac 1
quit
security-zone name trust
import interface gigabitethernet FWlan
quit
#
object-group ip address fw-lan
0 network subnet 2.2.2.0 255.255.255.0
#
object-group ip address lan-server
0 network subnet 20.2.2.0 255.255.255.0
#
object-group ip address fw-wan
0 network host address 100.1.1.2
#
object-group ip address wan-sslvpn-host
0 network subnet 100.1.1.0 255.255.255.0
#
object-group ip address sslvpn-ac
0 network subnet 10.1.1.0 24
#
secu ip
#
rule 0 name SSLVPN
source-zone Local
source-zone Untrust
source-zone Trust
destination-zone Untrust
destination-zone Local
destination-zone Trust
source-ip fw-wan
source-ip wan-sslvpn-host
source-ip lan-server
source-ip fw-lan
source-ip sslvpn-ac
destination-ip wan-sslvpn-host
destination-ip fw-wan
destination-ip fw-lan
destination-ip lan-server
destination-ip sslvpn-ac
#
3.Start Debugging SSLVPN.
<H3C>terminal monitor
<H3C>terminal debugging
<H3C>debugging sslvpn all
<H3C>system-view
[H3C]info-center enable
#
A common problem is that TLS negotiation fails. Solution: Customize the latest version of Inode to support TLS 1.2.
4.If debugging does not show any information, use following comand to check the session.
<h3c>display session table ipv4 destination-ip 100.1.1.2 destination-port 4430 verbose
if no session exists, mean that the device ,should check the connetcivity between pulic host and FW wan interface.
5.If we have Global NAT configuration existing, remember to check the NAT session.
<H3C>display nat session destination-ip 100.1.1.2 verbose
Key Configuration
1.display current
2.display security-zone
3.display security-policy ip
4.display session table ipv4 destination-ip 100.1.1.2 destination-port 4430 verbose
5.display nat session destination-ip 100.1.1.2 verbose
