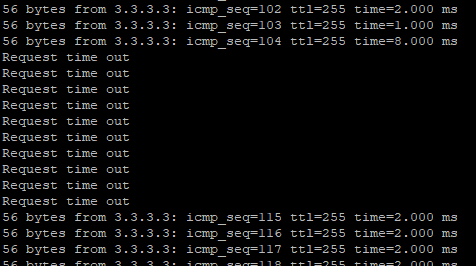
Network Topology
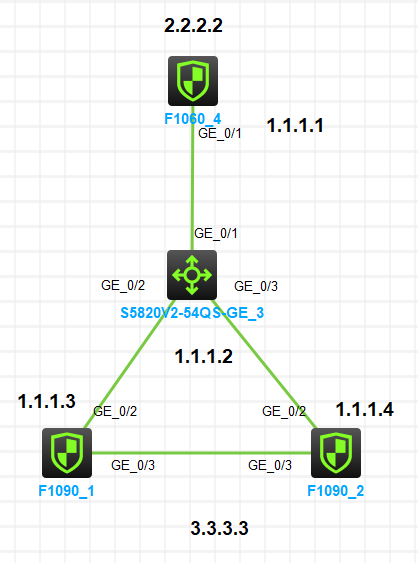
F1060 and F1090 establish the main mode ipsec, two F1090 do RBM+VRRP active/standby deployment, and the firewall loopback address acts as IPSec protected data stream.
Problem Description
When RBM does not switch, the IPSec tunnel is normal and the business is normal. When RBM switches, the IPSec breaks. After resetting Ike SA and IPSec SA on both sides, an IPSec tunnel can be established.
Process Analysis
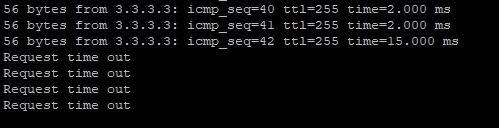
When RBM switches from active to standby, Ping fails:
Debug shows that no IKE SA message was discarded:
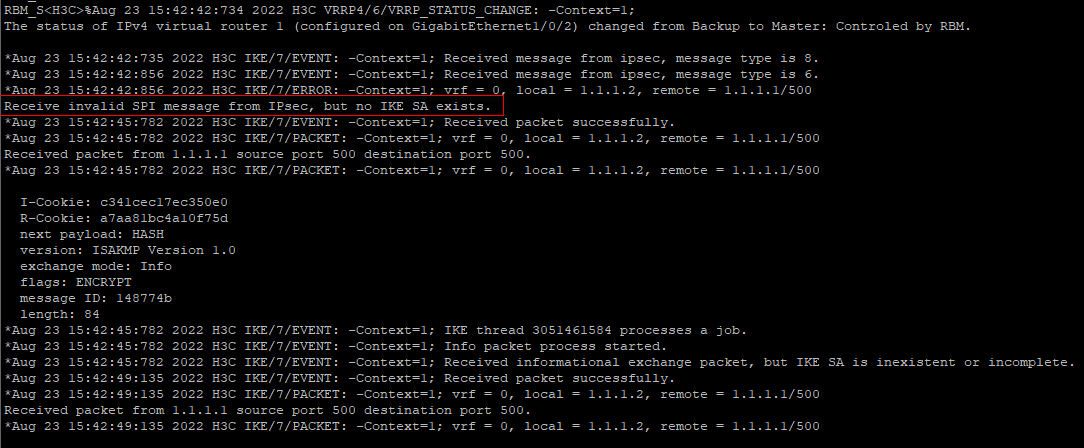
Because F1090 establishes IPSec with F1060 using VRRP virtual address, F1090 is insensitive to F1060 after RBM switching, so when pinging 3.3.3.3 from F1060, it still matches the IPSec SA negotiated with the original RBM master and does not go through the IPSec negotiation process again, resulting in the incompatibility of the opposite F1090 because there is no IKE sa. Here, communication is possible after retriggering ipsec negotiation from the F1090 side.
Solution
DPD detection needs to be configured on both F1060 and F1090, and DPD (Dead Peer Detection) is used to detect peer survival. This end actively sends DPD request message to the other end to check whether the other end is alive or not. If the end does not receive the DPD response message sent by the peer within the retry seconds of the DPD message, the DPD request message is retransmitted. If the DPD response message is not received after two retransmissions, the IKE SA and the corresponding IPsec SA are deleted.
After configuring dpd, RBM switchover, re-trigger ipsec negotiation, ping can communicate normally after the negotiation is completed:
ike dpd interval 3 retry 3 periodic