IPSEC Over GRE Tunnel using IKEv2 between H3C F1080 and CISCO ASA
- 0 Followed
- 0Collected ,1186Browsed
Network Topology
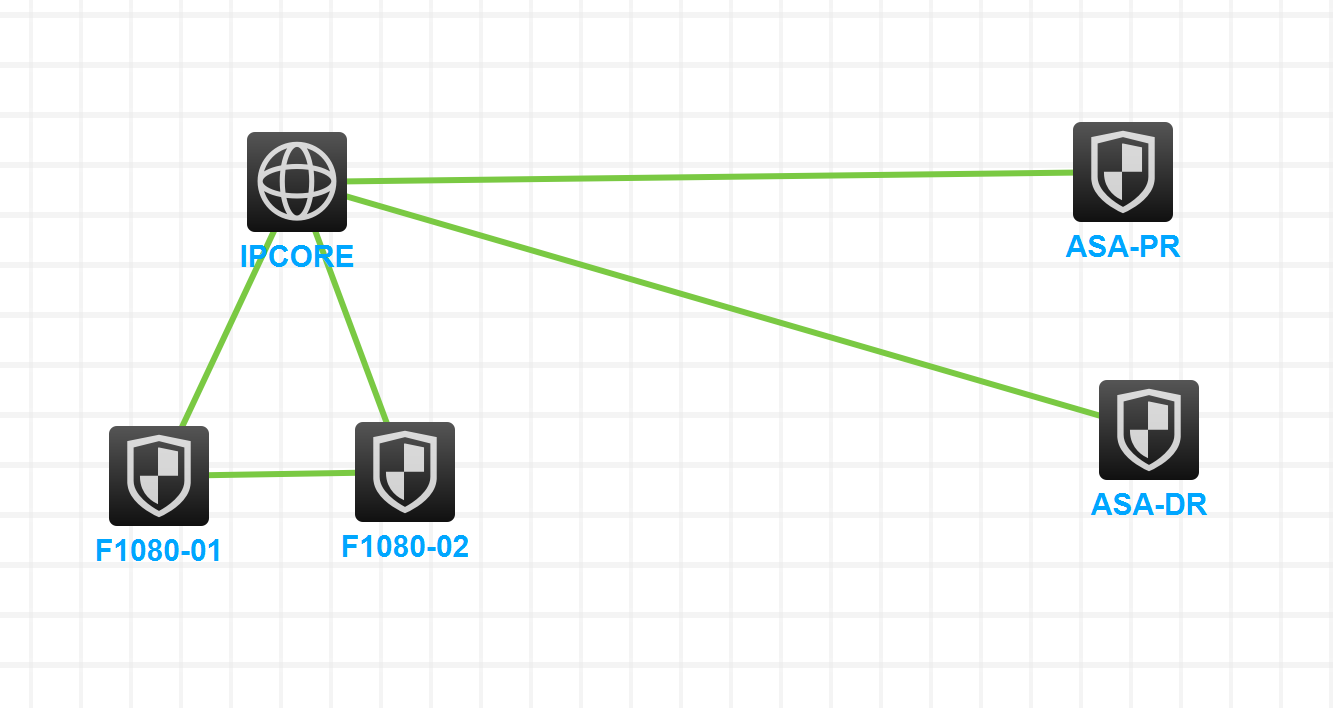
Topology
Problem Description
In XXX project we installed 2*F1080 Firewalls in IRF Mode. Configured 3*Contexts for 3 Different services and configured OSPF with Uplink IPCORE PE routers in each context.
Customer requests to establish IPSEC over GRE tunnel with remote CISCO ASA firewalls for some critical services.
As we have dual uplink to IPCORE so to avoid complexity I configured loopback interface on firewall and use it as local Peer address. and advertise this loopback in OPSF to IPCORE. And receive remote Peer IP as in OSPF
i created GRE tunnel and set source IP as This loopback and applied IPSEC policy on this tunnel
Process Analysis
I discussed with Customer that for this solution VTI tunnel or IPSEC over GRE would be best. So after customer agreement we configured IPSEC over GRE tunnel
Solution
acl advanced 3101
rule 0 permit ip source x.x.x.x 0 destination x.x.x.x 0
rule 5 permit ip source 193.x.x.x.x 0 destination x.x.x.x 0
#
acl advanced 3102
rule 0 permit ip source x.x.x.x 0 destination x.x.x.x 0
#
ipsec transform-set MFS_USSD
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha256
pfs dh-group2
#
ipsec policy MFS_USSD 10 isakmp
transform-set MFS_USSD
security acl 3101
remote-address x.x.x.x
ikev2-profile MFS_USSD
#
ipsec policy MFS_USSD_PR 10 isakmp
transform-set MFS_USSD
security acl 3102
remote-address x.x.x.x
ikev2-profile MFS_USSD_PR
#
ikev2 keychain MFS_USSD
peer MFS_USSD
address x.x.x.x .25 255.255.255.255
identity address x.x.x.x
pre-shared-key simple
#
ikev2 keychain MFS_USSD_PR
peer MFS_USSD_PR
address x.x.x.x 255.255.255.255
identity address x.x.x.x
pre-shared-key simple
#
ikev2 profile MFS_USSD
authentication-method local pre-share
authentication-method remote pre-share
keychain MFS_USSD
match remote identity address x.x.x.x 255.255.255.255
#
ikev2 profile MFS_USSD_PR
authentication-method local pre-share
authentication-method remote pre-share
keychain MFS_USSD_PR
match remote identity address x.x.x.x 255.255.255.255
#
ikev2 proposal MFS_USSD
encryption aes-cbc-256
integrity sha256
dh group14
#
ikev2 policy MFS_USSD
proposal MFS_USSD
#
ip route-static x.x.x.x 32 Tunnel2
ip route-static x.x.x.x 32 Tunnel1
Could you please also provide the opposite CISCO device configuration.
