Interface based IPSEC tunnel (VTI) between H3C Firewalls
- 0 Followed
- 0Collected ,3072Browsed
Test Item
Interface based IPSEC tunnel (VTI) between H3C Firewalls
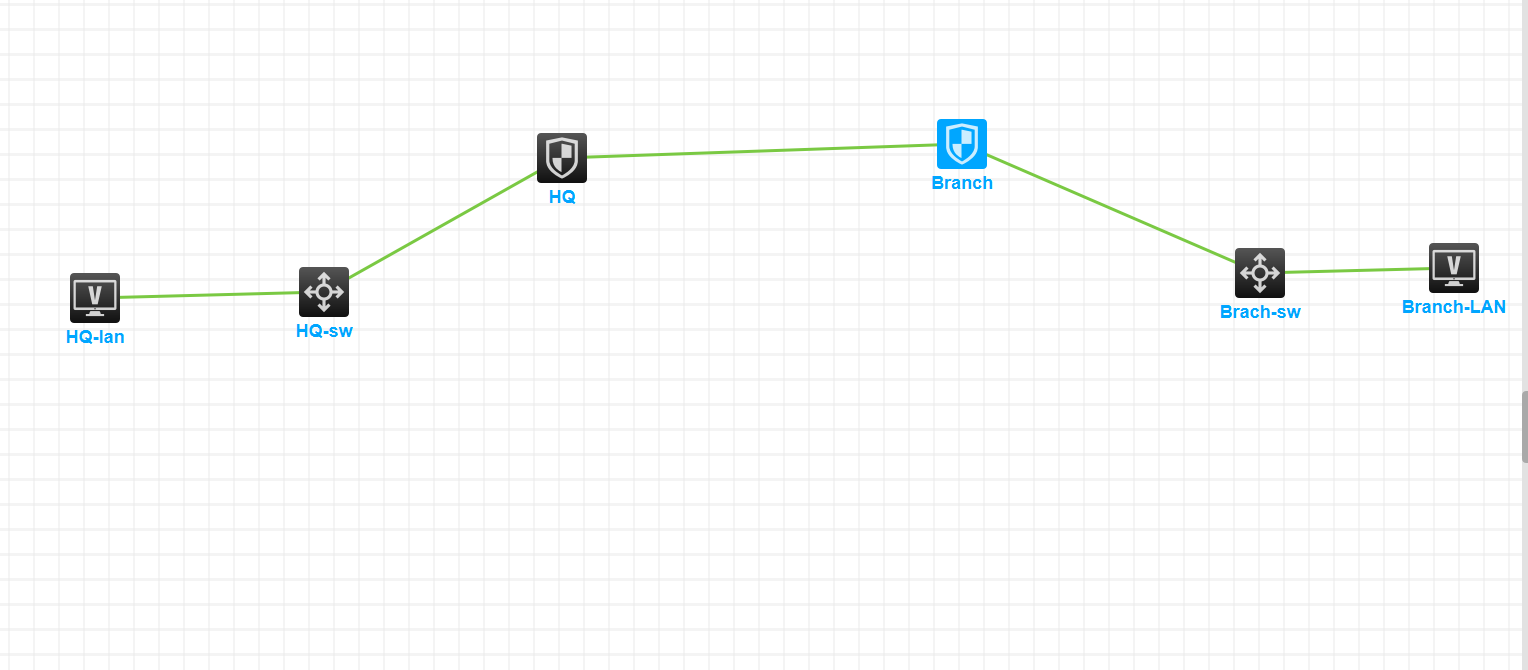
Test Topology
Topology
Test Process
Interface based IPSEC tunnel (VTI) between H3C Firewalls
Scenario
We have 2 sites (HQ & Branch). We want to protect traffic between these 2 sites by using VTI tunnel. We will configure OSPF for peer IP addresses reachability.
Ip addresses.
|
Local Device |
Local interface |
Remote device |
Remote Interface |
IP subnet |
|
HQ |
G0/0 |
Branch |
G0/0 |
10.1.1.0/30 |
|
HQ |
G0/1 |
HQ-LAN |
G1/0/1 |
192.168.1.0/24 |
|
Branch |
G0/1 |
Branch-LAN |
G1/0/1 |
172.1.1.1/24 |
IPSEC Peer Interfaces
|
Device |
Interfaces |
IP Address |
|
HQ |
Loopback0 |
1.1.1.1/32 |
|
Branch |
Loopback0 |
2.2.2.2/32 |
Configuration Steps
1.
HQ
interface GigabitEthernet1/0/1
port link-mode route
description *to-Branch*
combo enable copper
ip address 10.1.1.1 255.255.255.252
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
Branch
interface GigabitEthernet1/0/1
port link-mode route
description *To-HQ*
combo enable copper
ip address 10.1.1.2 255.255.255.252
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
2.
HQ
interface GigabitEthernet1/0/1
ospf 1 area 0.0.0.0
#
interface LoopBack0
ospf 1 area 0.0.0.0
Branch
interface GigabitEthernet1/0/1
ospf 1 area 0.0.0.0
#
interface LoopBack0
ospf 1 area 0.0.0.0
3.
HQ
ike keychain kechain
pre-shared-key address 2.2.2.2 255.255.255.255 key simple 123
#
ike profile prof
keychain kechain
local-identity address 1.1.1.1
match remote identity address 2.2.2.2 255.255.255.255
#
#
ipsec profile abc isakmp
transform-set trans
ike-profile prof
#
interface tunnel 1 mode ipsec
ip address 3.3.3.1 255.255.255.0
source 2.1.1.1.1
destination 2.2.2.2
tunnel protection ipsec profile abc
#
ip route-static 172.1.1.0 255.255.255.0 tunnel 1
Branch
Branch
ike keychain kechain
pre-shared-key address 1.1.1.1 255.255.255.255 key simple 123
ike profile prof
keychain kechain
local-identity address 2.2.2.2
match remote identity address 1.1.1.1 255.255.255.255
#
ipsec transform-set trans
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
#
ipsec profile abc isakmp
transform-set trans
ike-profile prof
#
interface tunnel 1 mode ipsec
ip address 3.3.3.2 255.255.255.0
source 2.2.2.2.2
destination 1.1.1.1
tunnel protection ipsec profile abc
#
ip route-static 192.168.1..0 255.255.255.0 tunnel 1
Test Result
display ike sa
display ipsec sa
ping LAN to LAN
