Network Topology
Topo: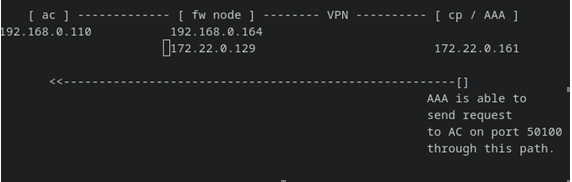
Problem Description
How to implement third-party portal server offline portal users instead of admin login access controller to do that
Process Analysis
Wireless controller support radius dynamic-author, and if radius server to send RADIUS Disconnect-Request to access controller and access controller can response Disconnect-ACK back to AAA.
Configuring the RADIUS DAS feature description:
Dynamic Authorization Extensions (DAE) to RADIUS, defined in RFC 5176, can log off online users and change online user authorization information.
In a RADIUS network, the RADIUS server typically acts as the DAE client (DAC) and the NAS acts as the DAE server (DAS).
When the RADIUS DAS feature is enabled, the NAS performs the following operations:
1. Listens to the default or specified UDP port to receive DAE requests.
2. Logs off online users that match the criteria in the requests, changes their authorization information, shuts down or reboots their access ports, or reauthenticates the users.
3. Sends DAE responses to the DAC.
DAE defines the following types of packets:
· Disconnect Messages (DMs)—The DAC sends DM requests to the DAS to log off specific online users.
· Change of Authorization Messages (CoA Messages)—The DAC sends CoA requests to the DAS to change the authorization information of specific online users.
The NAS searches for matching users based on the user identification information and device identification information in DAE requests. (The user identification information includes the username, user IP address, and Acct-Session-Id, and the device identification information includes the NAS IP address and NAS-ID.) If matching users are found, the NAS logs out the users or changes the authorization information for the users. If no matching users are found, the NAS replies with a NAK message. When DAE loose check is enabled, the NAS checks only part of the user identification information in a DAE request and does not check the device
Solution
Add dynamic-author server function
radius dynamic-author server
client ip 172.23.1.161 key cipher $c$3$GhGoXHKL4EsMz2dV9MmGjyBqmSpmNHZdGZ5QR8E=
The complete configuration is as follows:
wlan service-template attrelogix-wifi-staging
description test atlg
ssid AttreLogix-WiFi-Staging
portal enable method direct
portal domain atlg-domain
portal apply web-server "ATLG Apollo"
service-template enable
#
radius scheme atlg-radius
primary authentication 172.23.1.161 key cipher $c$3$5TouFyLZeINI8qQ+9DITcARJs8nEoR8/EQb/7Pc=
primary accounting 172.23.1.161 key cipher $c$3$R7ezYq72nLIYBFptqzwIa1afCLv4ULnGw2JlMPQ=
accounting-on enable
key authentication cipher $c$3$u7pxZdMsAnEnARvOtlfA9qXCM27V6E7DwbrYYmw=
key accounting cipher $c$3$YmyC4B7N5MGERdyPTX1sBPQV3yGO1v9Jb35NW+k=
user-name-format keep-original
nas-ip 192.168.110.2
attribute 30 format apmac-ssid delimiter colon
#
radius dynamic-author server
client ip 172.23.1.161 key cipher $c$3$GhGoXHKL4EsMz2dV9MmGjyBqmSpmNHZdGZ5QR8E=
#
domain atlg-domain
authentication default radius-scheme atlg-radius
authorization default radius-scheme atlg-radius
accounting default radius-scheme atlg-radius
#
portal free-rule 1 destination ip any udp 53
portal free-rule 1 description dns
portal free-rule 2 source ip any udp 53
portal free-rule 2 description dns
portal free-rule 3 source ip 103.13.75.198 255.255.255.255
portal free-rule 3 description portal
portal free-rule 4 destination ip 103.13.75.198 255.255.255.255
portal free-rule 4 description portal
#
portal web-server "ATLG Apollo"
url https://eaziwi5.attrelogix.com:8443/cp/attrelogix/h3c/
server-type cmcc
url-parameter mac source-mac
url-parameter ssid value AttreLogix-WiFi-Staging
url-parameter url original-url
url-parameter wlanuserip source-address
#
After the configuration is complete, the terminal can implement portal authentication.
Total portal users: 1
Basic:
AP
name: 8465-698d-f490
Radio ID: 3
SSID: AttreLogix-WiFi-Staging
Current IP address: 192.168.110.11
Original IP address: 192.168.110.11
Username: anonymous
User ID: 0x10000002
Access interface: WLAN-BSS1/0/5
Service-VLAN/Customer-VLAN: 1/-
MAC
address: 727b-1e75-0799
Authentication type: Normal
Domain name: atlg-domain
VPN
instance: N/A
Status: Online
Portal server: ATLG Apollo
Vendor: N/A
Portal authentication method: Direct
AAA:
Realtime accounting interval: 720s, retry times: 5
Idle cut: 600 sec, 10240 bytes
Session duration: 600 sec, remaining: 544 sec
Remaining traffic: N/A
Login time: 2023-04-06 04:38:53 UTC
Online time(hh:mm:ss): 00:00:56
DHCP IP pool: N/A
Web
URL: N/A
ACL&QoS&Multicast:
Inbound CAR: CIR 10485760 bps PIR 10485760 bps
CBS N/A (active, AAA)
Outbound CAR: CIR 10485760 bps PIR 10485760 bps
CBS N/A (active, AAA)
ACL
number/name: N/A
User profile: N/A
Session group profile: N/A
Max
multicast addresses: 4
Flow statistic:
Uplink packets/bytes: 212/47286
Downlink packets/bytes: 204/97885
Traffic average rate:
Uplink rate: 0 bytes/s
Downlink rate: 0 bytes/s
Total portal users:0
At the same time, we can also see the action of Force logout by RADIUS server by viewing the debug message:
*Apr 6 04:42:53:143 2023 attrelogix:h3c RADIUS/7/EVENT:
Received DAE request
packet successfully.
*Apr 6 04:42:53:144 2023 attrelogix:h3c RADIUS/7/PACKET:
User-Name="anonymous"
Acct-Session-Id="00000007202304060438530000000208109143"
Framed-IP-Address=192.168.110.11
Calling-Station-Id="72-7B-1E-75-07-99"
NAS-IP-Address=192.168.110.2
*Apr 6 04:42:53:144 2023 attrelogix:h3c RADIUS/7/PACKET:
28 6f 00 66 a0 10 70 d5 3c d7 bb 2c 81 04 94 dc
ee a8 8d d4 01 0b 61 6e 6f 6e 79 6d 6f 75 73 2c
28 30 30 30 30 30 30 30 37 32 30 32 33 30 34 30
36 30 34 33 38 35 33 30 30 30 30 30 30 30 32 30
38 31 30 39 31 34 33 08 06 c0 a8 6e 0b 1f 13 37
32 2d 37 42 2d 31 45 2d 37 35 2d 30 37 2d 39 39
04 06 c0 a8 6e 02
*Apr 6 04:42:53:144 2023 attrelogix:h3c PORTAL/7/EVENT:
User-SM[192.168.110.11]: Received
set-policy COA/POD notification.
*Apr 6 04:42:53:148 2023 attrelogix:h3c PORTAL/7/RULE:
DRV_USER_RULE:
L2 Interface =
WLAN-BSS1/0/5
L3 Interface =
WLAN-BSS1/0/5
VLAN =
1
SrcIP =
192.168.110.11
SrcMAC =
727b-1e75-0799
AuthorACL = 4294967295
Operation = 1
SetDrvFlag = 1
TrafficLevelNum = 0
TrafficLevelMap = 0x0
TrafficActionMap = 0x0
UserID = 268435458
vrfIndex = 0
AclMismatchAction= 0
*Apr 6 04:42:53:144 2023 attrelogix:h3c PORTAL/7/EVENT:
User-SM[192.168.110.11]: Notified Auth-SM to log off the user.
*Apr 6 04:42:53:144 2023 attrelogix:h3c PORTAL/7/FSM:
Auth-SM: Started to run.
*Apr 6 04:42:53:144 2023 attrelogix:h3c PORTAL/7/FSM:
Auth-SM [192.168.110.11]: Entered state Waiting.
*Apr 6 04:42:53:144 2023 attrelogix:h3c PORTAL/7/PACKET:
Portal sent 47 bytes of packet: Type=ntf_logout(8), ErrCode=0,
IP=192.168.110.11
*Apr 6 04:42:53:144 2023 attrelogix:h3c PORTAL/7/PACKET:
[ 5
TEXTINFO ] [
31] [Force logout by
RADIUS server]
*Apr 6 04:42:54:148 2023 attrelogix:h3c RADIUS/7/EVENT:
PAM_RADIUS: RADIUS accounting stopped.
*Apr 6 04:42:54:149 2023 attrelogix:h3c RADIUS/7/EVENT:
PAM_RADIUS: Sent accounting-stop request successfully.
*Apr 6 04:42:54:149 2023 attrelogix:h3c RADIUS/7/PACKET:
User-Name="anonymous"
NAS-Identifier="attrelogix:h3c"
NAS-Port=16777217
NAS-Port-Type=Wireless-802.11
NAS-Port-Id="0100000000000001"
NAS-IP-Address=192.168.110.2
Framed-Protocol=255
Calling-Station-Id="72-7B-1E-75-07-99"
Called-Station-Id="84-65-69-8D-F4-90:AttreLogix-WiFi-Staging"
Framed-IP-Address=192.168.110.11
Acct-Session-Id="00000007202304060438530000000208109143"
Acct-Multi-Session-Id="00000007202304060438530000000208009143"
Acct-Session-Time=241
Acct-Input-Octets=20788955
Acct-Output-Octets=16297464
Acct-Input-Packets=24555
Acct-Output-Packets=22393
Acct-Input-Gigawords=0
Acct-Output-Gigawords=0
Acct-Terminate-Cause=Admin-Reset //the radius process send accounting-stop request and reason is Admin-Reset.
