Network Topology
Topo:
Problem Description
Configure remote telnet user login for the network device, and require radius to deliver user role attributes to the user.
Process Analysis
The AAA protocol of H3C devices has a Vendor-Specific attribute (attribute 26) allows a vendor to define extended attributes. The extended attributes can implement functions that the standard RADIUS protocol does not provide.
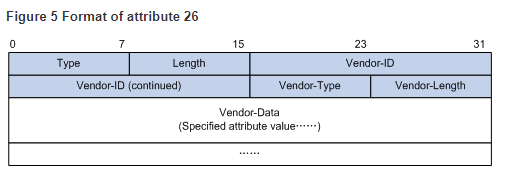
A vendor can encapsulate multiple subattributes in the TLV format in attribute 26 to provide extended functions. As shown in Figure 5, a subattribute encapsulated in attribute 26 consists of the following parts:
· Vendor-ID—ID of the vendor. The most significant byte is 0. The other three bytes contains a code compliant to RFC 1700.
· Vendor-Type—Type of the subattribute.
· Vendor-Length—Length of the subattribute.
· Vendor-Data—Contents of the subattribute.
Through Vendor-Specific attribute (attribute 26), IMC can authorizes User-Roles or user Exec-Privilege to telnet account.
Solution
Basic configuration:
[Switch]
#
radius scheme imc
primary authentication 172.16.1.70 key cipher $c$3$lrX2D5jHtng+zHlIryg6ciGqSN65PCpqiY4=
primary accounting 172.16.1.70 key cipher $c$3$vpIp6YXjENUxk5ecwjbai0vAGFnGb9fdSgo=
user-name-format without-domain
nas-ip 192.168.1.5
domain imc
authentication login radius-scheme imc
authorization login radius-scheme imc
accounting login radius-scheme imc
#
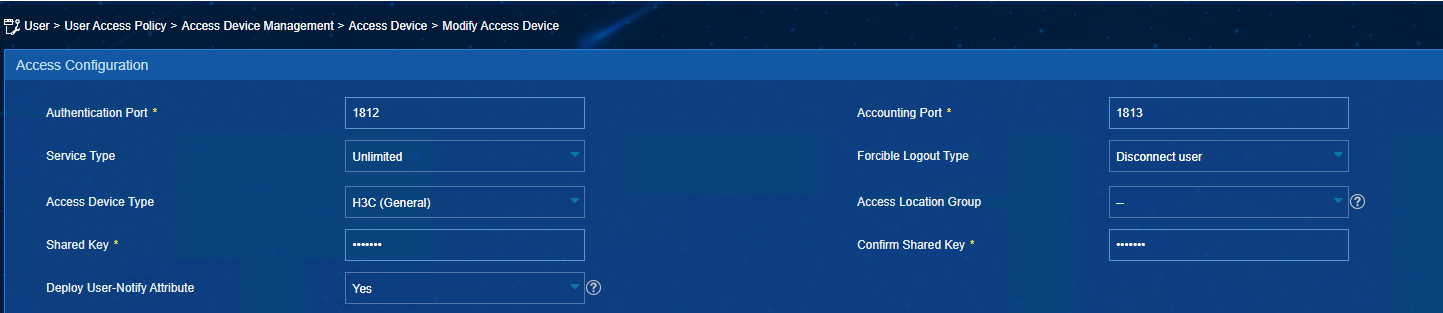
IMC add the access device.
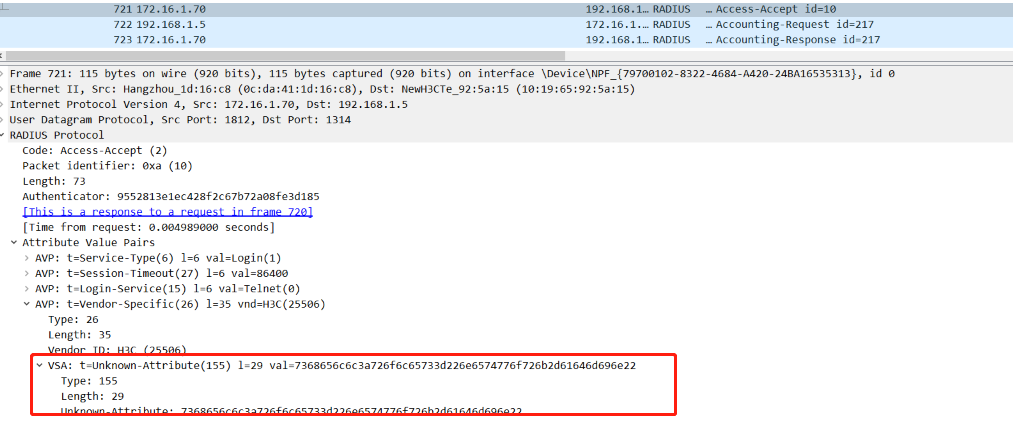
1. IMC authorizes user User-Roles
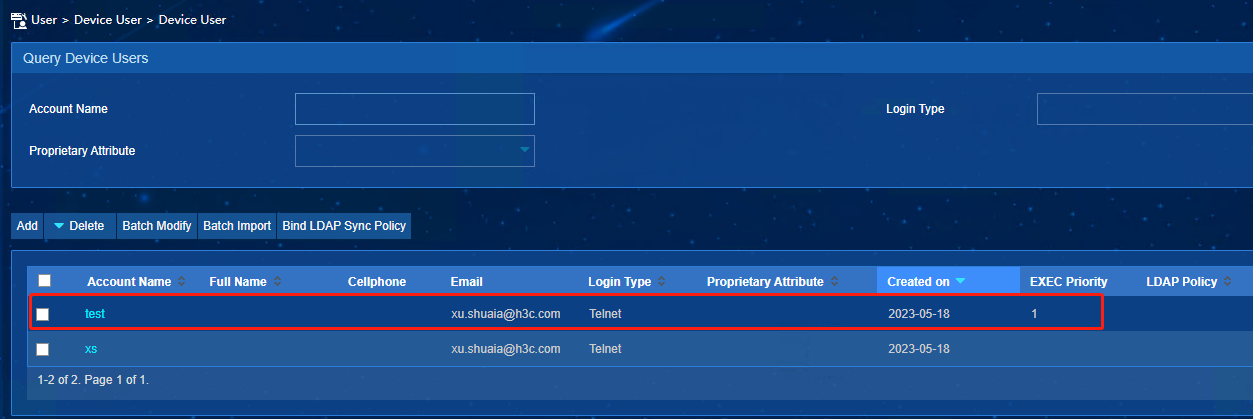
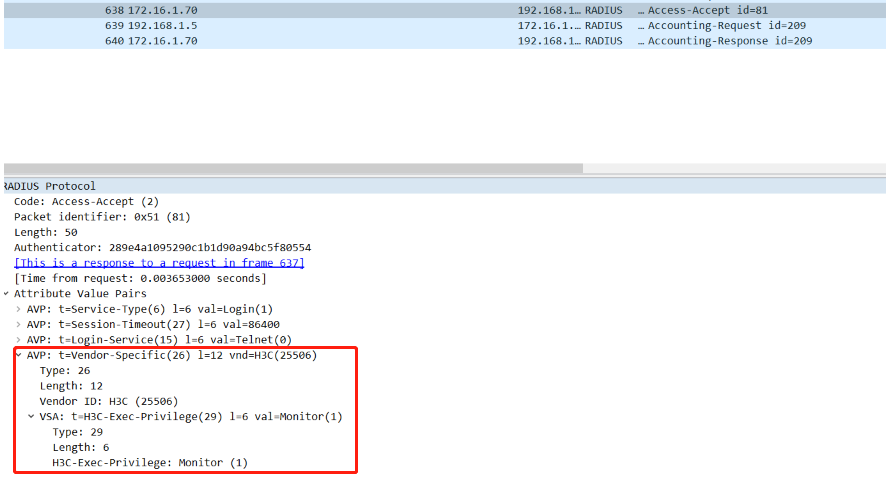
View the radius interaction debug log on the device, we can see that H3c-Exec-Privilege=1 is issued through radius authorization:
*May 18 11:30:33:656 2023 WX3840HDOWN RADIUS/7/PACKET:
Service-Type=Login-User
Session-Timeout=86400
Login-Service=Telnet
H3c-Exec-Privilege=1
*May 18 11:30:33:656 2023 WX3840HDOWN RADIUS/7/PACKET:
02 51 00 32 28 9e 4a 10 95 29 0c 1b 1d 90 a9 4b
c5 f8 05 54 06 06 00 00 00 01 1b 06 00 01 51 80
0f 06 00 00 00 00 1a 0c 00 00 63 a2 1d 06 00 00
00 01
we can view the H3c-Exec-Privilege=1 carried in packet capture.
2. IMC authorizes user network-admin role field
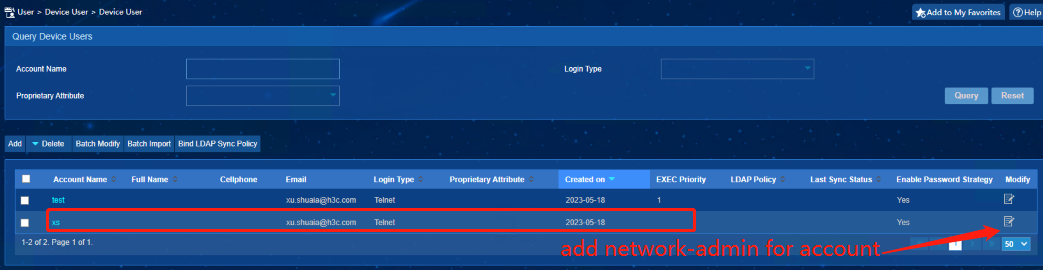
View the radius interaction debug log on the device, we can see that H3c-User-Roles="shell:roles="network-admin"" is issued through radius authorization:
*May 18 14:10:33:041 2023 WX3840HDOWN RADIUS/7/PACKET:
Service-Type=Login-User
Session-Timeout=86400
Login-Service=Telnet
H3c-User-Roles="shell:roles="network-admin""
*May 18 14:10:33:042 2023 WX3840HDOWN RADIUS/7/PACKET:
02 0a 00 49 95 52 81 3e 1e c4 28 f2 c6 7b 72 a0
8f e3 d1 85 06 06 00 00 00 01 1b 06 00 01 51 80
0f 06 00 00 00 00 1a 23 00 00 63 a2 9b 1d 73 68
65 6c 6c 3a 72 6f 6c 65 73 3d 22 6e 65 74 77 6f
72 6b 2d 61 64 6d 69 6e 22
we can view the
H3c-User-Roles="shell:roles="network-admin"" carried in packet capture.