Overview of Wireless 802.1x Escape Methods
- 0 Followed
- 0Collected ,1550Browsed
Network Topology
None
Problem Description
There are currently three configurations for wireless 802.1x escape:
1) Specify an alternative authentication method for none in the domain. When the current authentication method is invalid, attempt to use alternative methods to complete authentication in the order of configuration. This method requires the use of chap (dot1x authentication method chap) and must be combined with the inode client to be effective.
2) How to configure critical vlan (not recommended). This method can only be configured as non encrypted authentication, and 802.1X authentication in encrypted state does not support escape of this method. If not encrypted, 802.1X will lose the meaning of authentication, so we do not recommend using this method for 1 authentication escape.
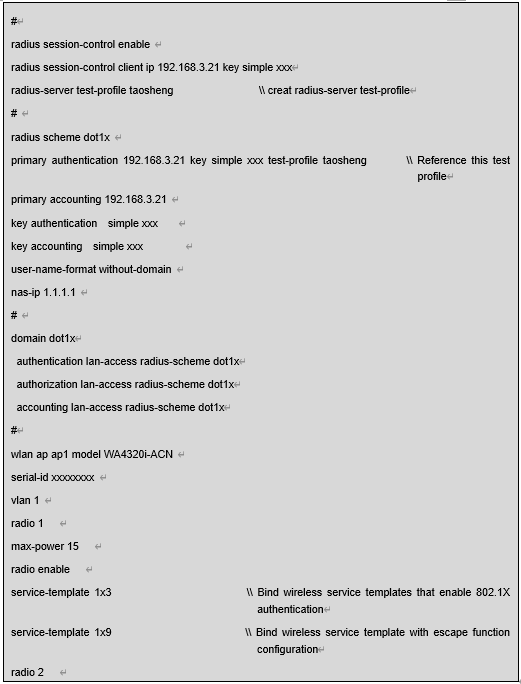
3) Escape service template method. When users use 802.1X authentication to access the network, use the fail permit template command to configure the escape service template in advance. When an escape occurs, the user service will be switched to the escape service template, and it is necessary to manually reconnect to the escape service template network before continuing to access the network.
Process Analysis
The escape service template method requires configuring the fail permit enable and fail permit template (refer to the final section of this case for specific configurations). Referring to the instructions for using these two commands in the wireless controller command manual, the following points can be found:
1) When users use 802.1X authentication to access the network, use the fail permit template command to configure the escape service template in advance. When an escape occurs, the user service will be switched to the escape service template. The escape service template is automatically enabled, but the terminal needs to manually reconnect to the escape service template before continuing to access the network.
2) The wireless service template used after escape and the wireless service template with 802.1X authentication enabled are two different service templates. The client security authentication location, client forwarding location, and client association location parameters configured under these two wireless service templates must be consistent.
3) To successfully escape, users must configure the RADIUS server detection template through the radius server test profile command. When it is detected that the RADIUS server is unreachable, users can escape. At the same time, it is recommended to configure the period for sending detection messages according to the actual situation. The shorter the period, the faster the response.
4) It is recommended to configure only one 802.1X authentication escape service template in the system. If multiple templates are configured, the first escape service template bound to Radio will take effect. It is recommended to configure the 802.1X authentication escape service template with AKM mode set to psk mode or without AKM mode, otherwise it may cause escape failure.
Solution
Key points of configuration: