Network Topology
None
Problem Description
The AC model of a certain office is WX3520H, the AP is WA6638, and the version is 5452P08. This office uses Windows built-in client with certificate for remote 802.1x authentication, and the authentication server is Cisco ISE.
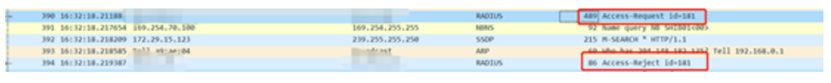
In the process of using the wireless network at this office, it is found that some terminals are suddenly disconnected when using the wireless network. Check the Artificial Intelligence for IT Operations data of the cloud simple network. It is found that 802.1X re authentication fails during the terminal disconnection, leading to the terminal disconnection. The reason code for the terminal disconnection is 5030.
Process Analysis
Looking at the deep parsing data of terminals on the cloud Jane network, it was found that the following process occurred:
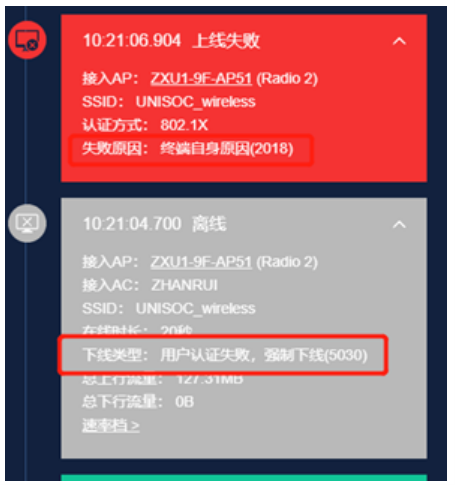

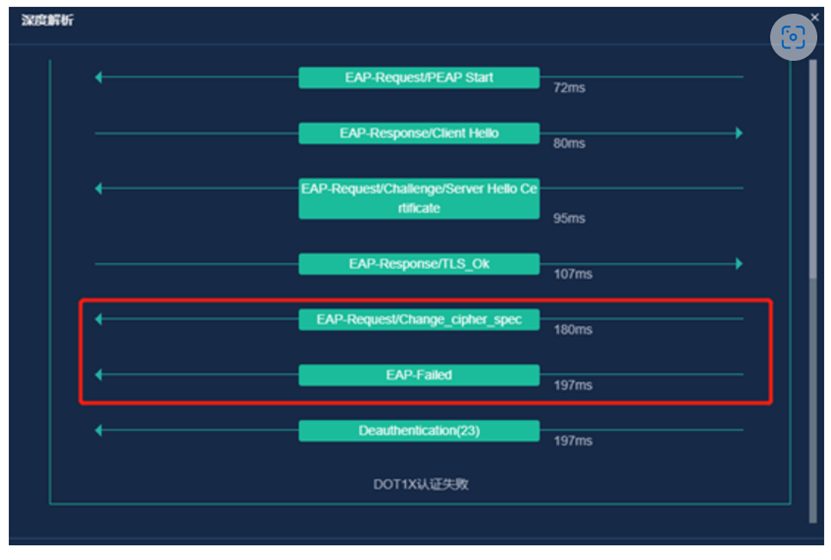
Normally, after receiving a challenge from the server, the terminal will reply with a response message to complete the authentication of the 802.1X certificate. However, the failure to complete this interaction process at the time of the fault indicates that an error occurred during the certificate interaction process. The wireless controller is in 802.1X relay mode and is responsible for forwarding authentication messages. It is necessary to query the specific cause of authentication errors from the AAA server. An error was found in the logs of the AAA server, as shown in the following figure:
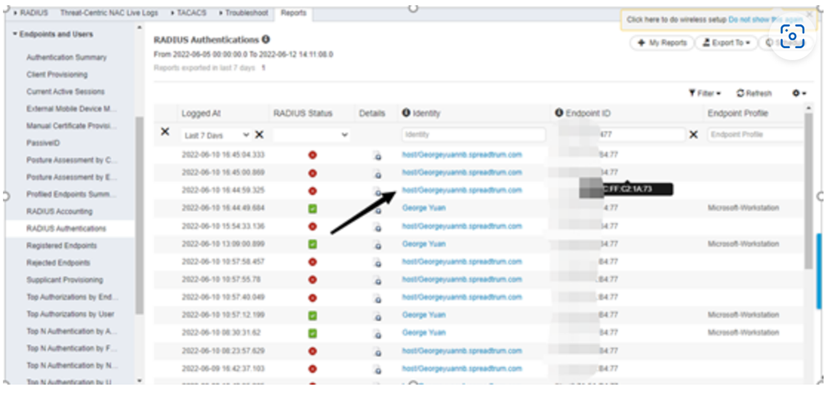
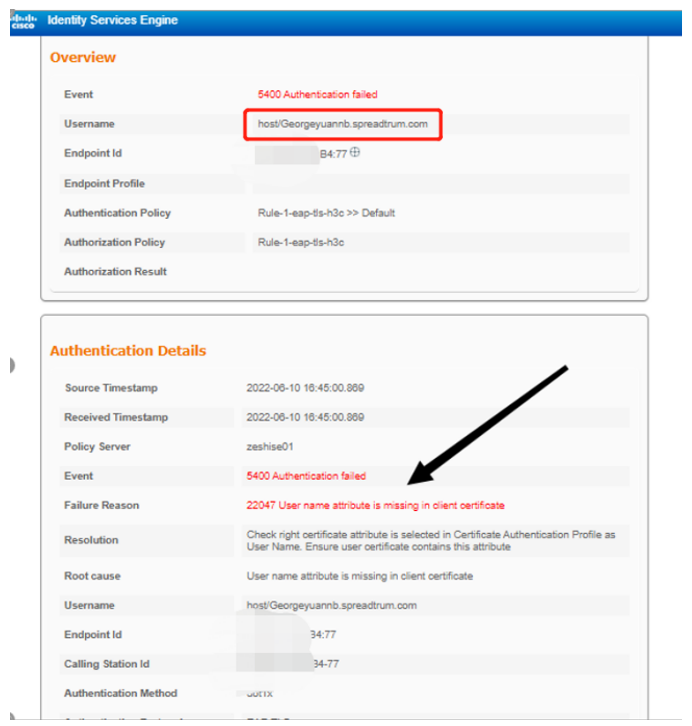
By capturing packets on the wired side of the AC - radius server, a similar phenomenon can also be found: when the terminal fails to re authenticate, the username used is the value generated by the default system name of the computer, and the server returns a reject value to inform the AC terminal that authentication has been rejected.
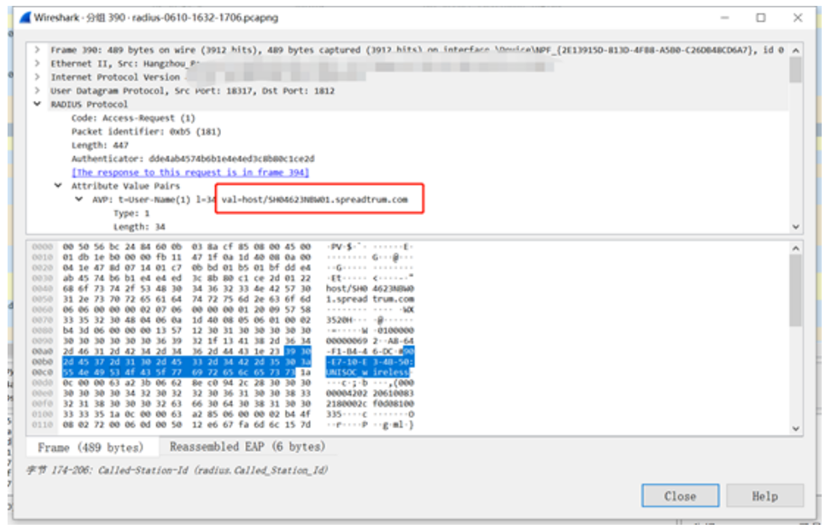
From the data on the AAA server and packet capture data, it can be seen that the authentication failed terminal once logged in with a non domain name account, which is the value generated by the default system name of the computer; The server-side strategy only allows domain name account login, so the server returns a Reject value to inform the wireless device that the terminal authentication has been rejected.
Investigating the reason why the computer name was logged in as an account name, it was found that there is a configuration in the wireless configuration of the computer: 802.1X settings - specified authentication mode - username or computer authentication.
Most Win10 computers, if they do not pay attention to this detail during initial setup, will default to selecting "User or Computer Authentication". However, this "User or Computer Authentication" setting is used in some special situations, such as waking up after hibernation, turning on the computer, and when the user certificate on the computer fails to be selected, the local computer certificate is then selected. Obviously, the AAA server will consider this to be an illegal login account ID.
The 802.1X settings of most WIN10 models in this office are in this situation, and WIN7 computers have avoided this issue due to the initialization setup step.
Solution
It is necessary to adjust the WiFi settings of the computer network card, modify the settings of 802.1X, and adjust them to "User Authentication".
