Network Topology
None
Problem Description
Using Google mobile phones for wireless 802.1x authentication (eap pea/mschapv2) on site, certificate authentication error reported during authentication.
Process Analysis
1) Check the certificate configuration on the eia side to see if the preset certificate has been imported. The preset certificate has been imported on site and the certificate verification is valid.
2) Collect UAM debug logs and check the corresponding debug logs for errors such as internal errors on the client server or issues with phone settings.
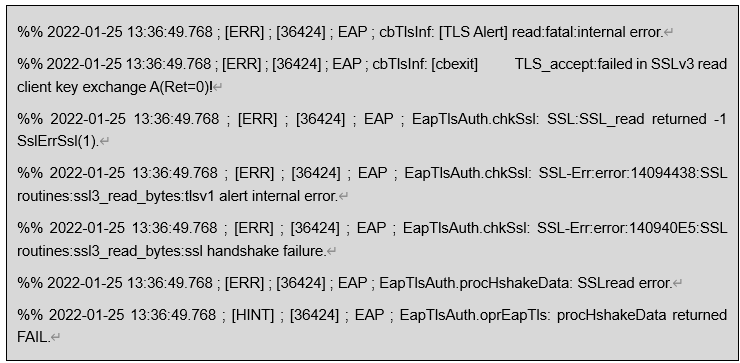
3) Generally, for EAP peap/mschapv2 authentication, the client does not need to verify the server certificate, and only needs to configure the root certificate and server certificate on the EIA side. But the scene was a Google phone, and according to the instructions on the phone"s official website, there is a prompt that starting from Android version 11, the client side cannot choose not to verify the CA certificate, which means that the client must have a CA certificate.
4) Because the CA certificate on the EIA side is a purchased commercial certificate, this certificate has already been preset on the Google mobile phone on-site. Therefore, there is no need to import additional certificates. If the phone does not have this certificate preset, you can import the CA certificate provided by eia. The CA certificate provided by eia has two levels of authorities (topRoot CA and ScandRoorCA, both of which need to be imported. When selecting, you can choose a second level CA).
5) After pre setting the EIA CA certificate on site, there was still a certificate authentication error. After inspection, it was found that it was caused by a domain name configuration error.
Solution
Select the authentication CA certificate on the terminal. If the certificate is not imported on the terminal, a separate certificate needs to be imported.
