Experience case of handling SSLVPN service failure due to FW traffic hitting Outbound LLB
- 0 Followed
- 0Collected ,4719Browsed
Network Topology
FW serves as an Internet egress and serves as an SSL VPN gateway.
Equipment model: F1000-AI-25
Software version: Release 8860P27
Networking: PC----Internet------FW--------Intranet server
Problem Description
After the PC dials up SSLVPN, it cannot ping the intranet server, but the FW intranet port can ping the server.
Process Analysis
1.
[fw]display session table ipv4 source-ip 10.10.10.10 verbose
Slot 1:
Initiator:
Source IP/port: 10.10.10.10/1
Destination IP/port: 192.168.1.1/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: SSLVPN-AC1
Source security zone: test
Responder:
Source IP/port: 192.168.1.1/24786
Destination IP/port: 17.17.17.17/0
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet1/2/3
Source security zone: test1
State: ICMP_REQUEST
Application: ICMP
Rule ID: -/-/-
Rule name:
Start time: 2023-09-07 22:58:54 TTL: 57s
Initiator->Responder: 3 packets 180 bytes
Responder->Initiator: 0 packets 0 bytes
2.
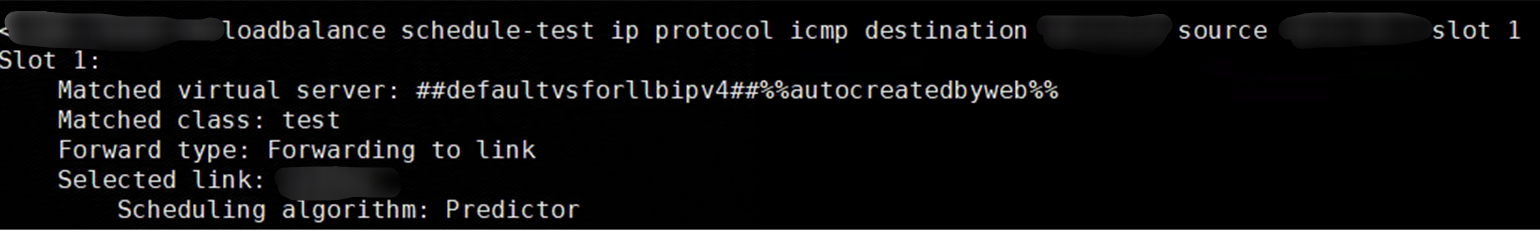
Solution
Since the on-site SSL VPN traffic will also preferentially match the Outbound LLB, you need to configure the load balancing policy so that the SSL VPN traffic from the PC accessing the intranet server does not perform load balancing actions.
#
loadbalance action sslvpn type link-generic
forward all (Forwarded directly according to the routing table)
#
Note: The incoming interface (Internet interface) of ICMP traffic needs to enable ip last-hop hold, so that forward all is not required for return packets.
<Sysname> system-view
[Sysname] interface gigabitethernet 1/0/1
[Sysname-GigabitEthernet1/0/1] ip last-hop hold
