Wireless 802.1x Authentication Abnormal Drop Experience Case
- 0 Followed
- 0Collected ,3880Browsed
Network Topology
Null
Problem Description
The client completes 802.1x authentication, obtains the ip, and there is client online session, and it can access the internet. However, it will drop out abnormally in 1~2 minutes, with reason code 5025, and will not reconnect.
# wlan service-template 1
ssid Everest vlan 5
client-security authentication-location central-ac
quick-association enable akm mode dot1x
cipher-suite ccmp
security-ie rsn
client-security authentication-mode dot1x
dot1x handshake enable
dot1x re-authenticate enable
dot1x domain zjccb
service-template enable
#
Process Analysis
1. Debugging the AP ar5drv , we found that the client can normally complete 802.1x authentication, as well as four handshakes.
debugging ar5drv 1 packet all mac H-H-H verbose
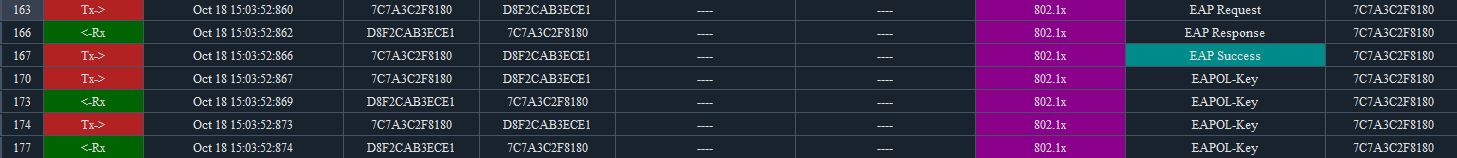
2. In the subsequent presence of EAP Request/Resonse at intervals that are different from regular 802.1x authentication, and at the end the deauth frame is sent by the device.
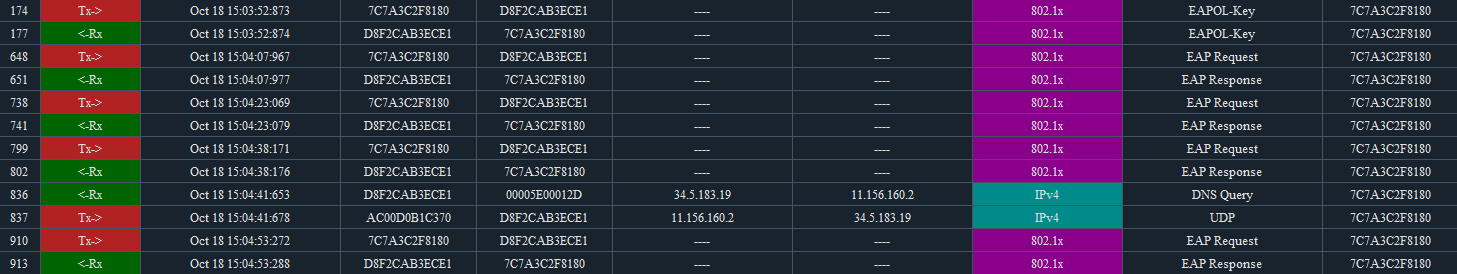
3. I troubleshooted the service template configuration and eventually found the dot1x handshake enable and dot1x re-authenticate enable commands, both of which are usually not enable by default.
① dot1x handshake enable
② dot1x re-authenticate enable
Both of the above commands will send a message to the terminal after the client has been successfully authenticated, both of which will detect the user's online status. However, because the device does not reply to the user any more after a successful handshake of dot1x, causing some clients to re-authenticate or go offline after a period of time.
Solution
undo dot1x handshake
undo dot1x re-authenticate
Tips:
those command will force client offline
dot1x handshake enable
dot1x re-authenticate enable
