★ ★Configuring domain name-based security policy does not take effect
- 0 Followed
- 0Collected ,3539Browsed
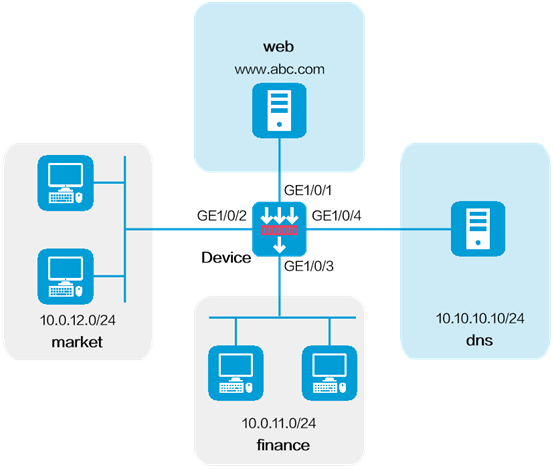
Network Topology
Example:
Problem Description
According to the configuration example, the customer can use a separate host name in the IPv4 address object group to successfully access the website, such as www.baidu.com. However, if the address with a wildcard is configured, the access cannot be successful, such as *.baidu.com.
Process Analysis
There are two solutions for firewall configuration based on domain name security policy:
Solution 1: Configure the domain name object group directly on the device and call the object group in the security policy. After the device detects the object group configuration based on the host name, it will actively request the IP address corresponding to the domain name from the DNS server. The table entries are parsed again after aging.
Examples are as follows:
#
object-group ip address baidu
0 network host name www.baidu.com
#
dns server A.A.A.A ---- The dns server must be configured, otherwise the device cannot resolve the IP corresponding to the domain name in the address object group.
#
This solution is simple to configure. Since the device essentially performs security policy checks based on IP, it is necessary to ensure that the domain name resolution results of the terminal and the device itself are consistent. You can use the following command to view the parsing results:
RBM_Pdisp dns host Type:
D: Dynamic S: Static
Total number: 1
No. Host name Interface Type TTL QType IP addresses
1 www.baidu.com - D 3146 A a.a.a.a ---- Ensure that the parsing results on the device are consistent with the parsing results on the terminal
RBM_Pdisp object-group ip host object-group-name baidu Object group : baidu
Object ID : 0
Host name : www.baidu.com
VPN instance : -
Updated at : 2024-01-03 15:43:04
IP addresses :
a.a.a.a
It should be noted that if the device does not act as a DNS proxy, that is, the terminal"s DNS points to a separate DNS server instead of the device, security policy restrictions cannot be imposed on ambiguous domain names (such as *.baidu.com). This leads to solution two.
Solution 2: The device acts as a DNS proxy, and the terminal’s DNS points to the FW device. The FW device needs to add the following configurations:
#
dns proxy enable --- Enable dns proxy function
#
In actual use on the existing network, the above solution may encounter the following problems:
1. Domain names age too quickly. The terminal"s access request is continuous, and the IP corresponding to its domain name has not changed. However, the IP reparsed on the device is new and does not match the two sides.
Solution: You can try configuring the dns cache ttl command to adjust the aging time of domain name table entries.
2. The resolution results of a certain domain name on the terminal and the device are inconsistent, causing the policy to fail.
Solution: This problem is related to the behavior of the DNS server. DNS requests for the terminal and FW device return different resolution results. You can try to configure a DNS proxy on the device to solve the problem.
Solution
FW is essentially based on IP matching security policies, and it is necessary to ensure that the terminal DNS resolution results are consistent with the FW device.
