★Firewall NAT hairpin troubleshooting methods
- 0 Followed
- 0Collected ,1511Browsed
Network Topology
The networking is simplified as follows:
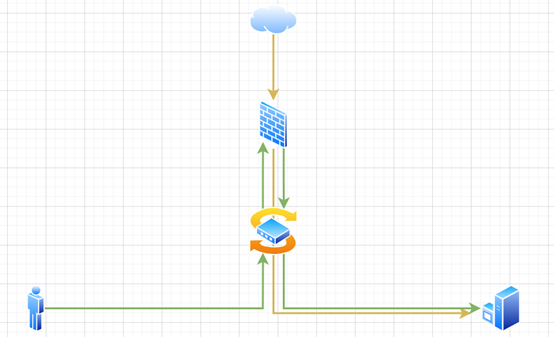
Function Description:
The NAT hairpin function is used to meet the need for access between users on the intranet or
between users and servers through NAT addresses. When NAT hairpin is enabled,
the internal network side interface of the packet will translate the source address
and destination address of the packet at the same time.
The green solid line in the figure above describes the
access path of the NAT hairpin function, and the path described by the yellow
solid line is the normal DNAT access path, that is, the server in the internal
network provides corresponding services to the external network.
Problem Description
The customer has a need for NAT hairpin.
After configuring it according to the configuration guide, intranet users
cannot access the intranet server using the public address.
Process Analysis
Principle description:
1. Configure nat hairpin enable directly
under the internal network port. This configuration is equivalent to copying
the public network port configuration to the internal network port.
After the traffic comes in from the
internal network port, it needs to go through the following process: SNAT---security
policy---DNAT---find route and forward. The address after SNAT is the public
network address.
2. Deliver the dnat+snat configuration to
the internal network port. The example is as follows:
#
interface Ten-GigabitEthernetx/x/x
port link-mode route
nat outbound
nat server global A.A.A.A inside a.a.a.a
#
After the traffic comes in from the
internal network port, it will go through the following process, DNAT---find
routing and forwarding---security policy---SNAT---find routing and forwarding.
It should be noted that the address after SNAT is the internal private network
address.
3. Use global NAT (nat global-policy), for
example:
#
nat global-policy
#
rule name test
description test
source-zone Trust
destination-ip host A.A.A.A
action snat easy-ip
action dnat ip-address a.a.a.a
counting enable
#
After the traffic comes in from the
internal network port, it will go through the following process: DNAT---find
route---security policy---SNAT---find route and forward. The address after SNAT
is also the internal private network address.
Regardless of the conversion method
mentioned above, if a problem occurs under the premise of understanding the
basic principles, first locate the corresponding NAT configuration and check the
corresponding NAT session to see if the NAT conversion is normal
(display session table ipv4 source-ip X.X.X.X destination-ip Y.Y.Y.Y verbose (must add verbose!)).
If there is no session, adjust the
filtering conditions to prevent omissions; if there is still no session after
adjustment, there is a high probability that it may be blocked by the security
policy.
If there is a corresponding session, check
whether the NAT conversion is normal and whether snat and dnat conversion are
performed in the Responder direction. If there are corresponding conversions,
pay attention to whether the packet sending interface is accurate.
The most common problem encountered in
existing networks is routing problems. Packets are sent from the public network
port, resulting in service interruption. Here you need to pay attention to whether the
internal network port has policy routing configuration.
If the problem cannot be found by simply
viewing the session, you need to further write acl to debug and troubleshoot
the cause. The rules corresponding to acl contain all conversion processes as
much as possible. Examples are as follows:
client_ip----A.A.A.A (bidirectional)
snat site---A.A.A.A (bidirectional)
snat site---a.a.a.a (bidirectional)
client_ip----a.a.a.a (bidirectional)
If you don’t understand the NAT hairpin
conversion process, it is recommended that the above rules be added to the
corresponding ACL. Common debugs are as follows:
<FW>debugging ip packet acl 3XXX # Check the specific interface and slot from which the packet is received and sent.
<FW>debugging ip info acl 3XXX # If there is packet loss, the specific module of the information packet loss will be printed. If there is no packet loss, it will not be printed.
<FW>debugging aspf packet acl 3XXX # If the packet status is illegal, it will be displayed as being discarded by aspf. You need to check whether the traffic is consistent.
<FW>debugging security-policy packet ip acl 3XXX # If it is an object policy, use object-policy, if it is packet filtering, use packet-filter
<FW>debugging nat packet acl 3XXX #View nat session status
If there is no session but debug packets are received, you still need to collect:
<FW>debugging session session-table event acl 3XXX # You can view the specific situation of the session being deleted.
Solution
Understand
the implementation principle of NAT hairpin, sort out the traffic forwarding
path, and ensure that the packet forwarding interface is normal.
It
is recommended to configure the last hop holding function on the internal
network port. The corresponding command is as follows:
Use ip last-hop hold to enable last hop holding.
Use undo ip last-hop hold to disable last hop holding.
Syntax
ip last-hop hold
undo ip last-hop hold
The following compatibility matrix shows the support of hardware platforms for this command:
Default
Last hop holding is disabled.
Views
Layer 3 Ethernet interface view
Layer 3 Ethernet subinterface view
Predefined user roles
network-admin
context-admin
Usage guidelines
Last hop holding implements symmetric routing. It tracks the last hop MAC address for the first incoming IP packet of a connection, and it sends the return packets to the hop that transmits the request.
Last hop holding is based on fast forwarding entries. If the MAC address of a last hop changes, this feature can function correctly only after the fast forwarding entry is updated for the MAC address.
Examples
# Enable the last hop holding feature.
[Sysname] interface gigabitethernet 1/0/1
[Sysname-GigabitEthernet1/0/1] ip last-hop hold
