Cloud ap batch offline
- 0 Followed
- 0Collected ,1166Browsed
Network Topology
cloud mode ap
switch ---- aps
Problem Description
A large number of AP frequent on-line and off-line problems;
the terminal can"t access the WLAN when the failure occurs, and the terminals are also unable to access the internet after accessing WLAN.
Process Analysis
Through continuous use of the "display interface" command to inspect packet counts on the interface, we observed that the volume of abnormal unicast packets sent from the switch to the AP was approximately 2 million packets per second(pps).
It had been found a large number of abnormal unicast packets, being sent to the AP in the VLAN 10, causing disruption to normal AP operations.
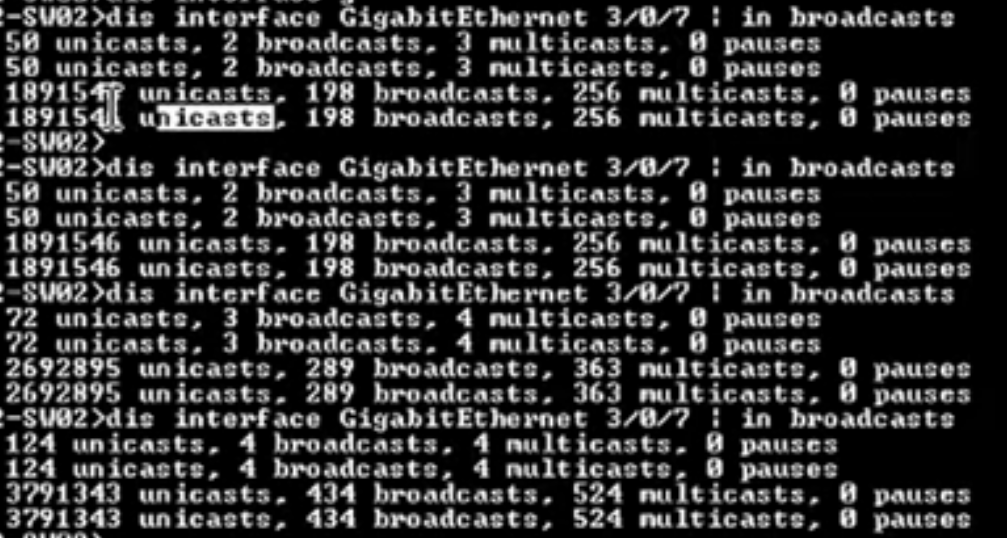
After blocking VLAN 10, the AP returned to normal operation. To ensure that wired and wireless devices used different VLANs: wireless VLAN 11 and wired VLAN 40.
Another surge in AP disconnections few days later. It was traced to the AP receiving a large number of unknown unicast packets on VLAN 11.
During the issue, it was observed that the MAC address "****-****-****" of the abnormal terminal frequently drifted between two long-distance aps.
<h3c> dis mac-address | in ****-****-****
And at the same time, it was sending large number of unknown unicast packets to the network, causing the disruption to normal AP operations. Find the source mac and destination mac in packet capture.
While threre is a fake mac-address which is not exist in the network at all. Refer to the record above, we checked mac-address on the core switch and there is no mac-address matched.
According to the mechanism of switch, it would flood the packets with unknow destination mac-address to all the ports of switch. So all the attacking packets were transferred to every AP which caused the disruption of WLAN.
In other words, the attacker exploited the mechanisms of the switch to launch a massive attack by flooding the network with abnormal packets, targeting all APs in the network.
Solution
For prevent the customer’s network from the attacking of ****-****-**** and other possible attack of unknow unicast in the future.
- We have set the blacklist for the WLAN access on the Cloudnet. The attacker ****-****-**** can"t access the WLAN anymore.
- Set the "unicast-suppression pps 100" on every downlink ports on the access switches.
Use unicast-suppression to enable unknown unicast storm suppression and set the unknown unicast storm suppression threshold as 100. With the help of this command, the other unknow unicast would not affect the customer network in the future. Refer to: unicast-suppression. - Provide the packets filter configuration to block the mac-address from the wired clients. If the customer need block any mac-address from the wired network can set the following configuration on downlink of the core switch.
Take mac-address 000f-e200-0000 as an example:
#
acl number 4001
rule 0 deny source-mac 000f-e200-0000 ffff-ffff-ffff
#
interface GigabitEthernet1/0/1
packet-filter 4001 inbound
packet-filter 4001 outbound
#
And if customer need block additional mac-address 000f-e200-0001, only need add the additional mac address in the ACL 4001 as following:
#
acl number 4001
rule 0 deny source-mac 000f-e200-0000 ffff-ffff-ffff
rule 1 deny source-mac 000f-e200-0001 ffff-ffff-ffff
#
