Example of configuring different VPN instances to communicate with each other and ensure Internet access
- 0 Followed
- 0Collected ,2874Browsed
Network Topology
Requirements:
PC1 and PC2 belong to different VPN instances. Both PCs can access the Internet at the same time and ensure intercommunication.
Topology:
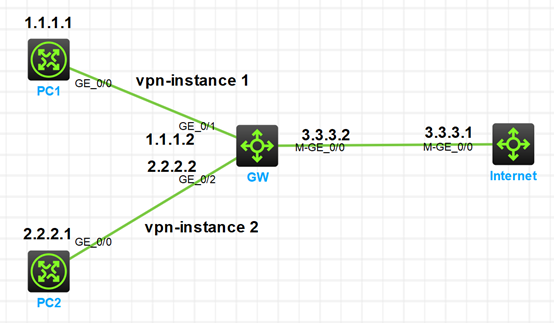
Configuration Steps
Create two instances:
#
interface Vlan-interface1
ip binding vpn-instance 1
ip address 1.1.1.2 255.255.255.0
#
interface Vlan-interface2
ip binding vpn-instance 2
ip address 2.2.2.2 255.255.255.0
#
interface Vlan-interface3
ip address 3.3.3.1 255.255.255.0
#
1. First, enable VPN instance 1 and VPN instance 2 to access the public network:
Take VPN instance 1 as an example, add the default route for VPN 1 to access the public network:
[h3c] ip route-static vpn-instance 1 0.0.0.0 0 3.3.3.2 public
Add a return route:
[h3c] ip route-static 1.1.1.1 32 vpn-instance 1 1.1.1.1 //The destination address is a specific address, so it is 1.1.1.1 32
The configuration of VPN instance 2 is the same as that of VPN instance 2.
2. Inter-access between VPN instances:
Take PC1 accessing PC2 as an example (1.1.1.1 ping 2.2.2.1):
Add a static route for PC1 to access PC2:
[h3c] ip route-static vpn-instance 1 2.2.2.1 32 vpn-instance 2 2.2.2.1
Add a return route:
[h3c] ip route-static vpn-instance 2 1.1.1.1 32 vpn-instance 1 1.1.1.1
This way, the two PCs can communicate with each other
Key Configuration
Pay attention to whether the VPN instance is placed first or last when writing static routes.
If the traffic inbound interface is not bound to a VPN instance, the incoming message will search the global routing table. You can add the VPN instance to which the message needs to be introduced after the static route destination address.
If the traffic inbound interface is bound to a VPN instance, the incoming message will search the corresponding VPN instance routing table. At this time, the VPN instance should be placed first.
