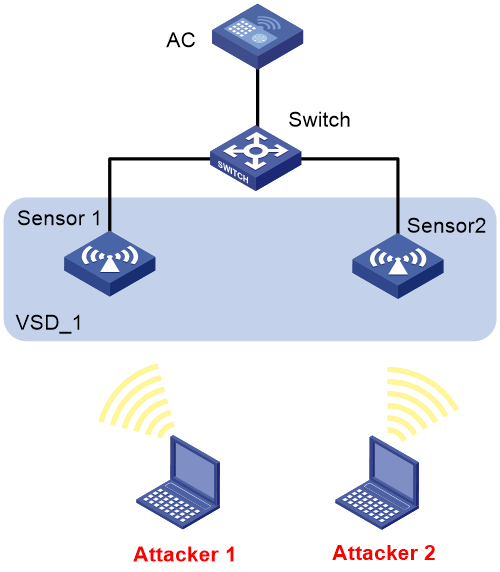
Network Topology
Topology:
Problem Description
A certain site uses WIPS for countermeasures, but it is found that WIPS has a better countermeasure effect on hotspots opened by Android terminals, but a poor countermeasure effect on hotspots opened by Apple terminals. Apple terminals have turned off random macs, and the iOS system is 16.5.
Process Analysis
1.
wips
#
ap-classification rule 1
ssid equal Test
#
classification policy 1
apply ap-classification rule 1 rogue-ap severity-level 100
#
countermeasure policy 1
countermeasure rogue-ap
countermeasure enhance
#
detect policy 1
ap-spoofing quiet 360
client-spoofing
client-association fast-learn enable
#
virtual-security-domain vsd1
apply classification policy 1
apply countermeasure policy 1
#
client-proximity-sensor random-mac-report enable
2.
[DX-NH-WX3520X-AC1-wips-dtc-1]display wips virtual-security-domain vsd1 device | include 5c1d
d272-907b-5c1d AP Rogue 00h 00m 28s 6 6 Inactive
[DX-NH-WX3520X-AC1-wips-dtc-1]dis wips virtual-security-domain vsd1 countermeasure record | in 5c1d
d272-907b-5c1d AP Class AP2 2 2023-06-25/16:57:12
d272-907b-5c1d AP Class AP3 2 2023-06-25/17:11:42
d272-907b-5c1d AP Class AP2 2 2023-06-25/17:11:42
d272-907b-5c1d AP Class AP3 2 2023-06-25/17:11:42
d272-907b-5c1d AP Class AP2 2 2023-06-25/17:14:24
d272-907b-5c1d AP Class AP2 2 2023-06-25/17:14:24
d272-907b-5c1d AP Class AP2 2 2023-06-25/17:14:24
3.
Apple hotspot mac: d272-907b-5c1d
Test phone mac: 9cbc-f08f-c111
Air interface packet capture shows that the AP impersonates the mac of the mobile terminal and continuously sends deauth messages to the Apple hotspot, but in fact the terminal can still connect stably.
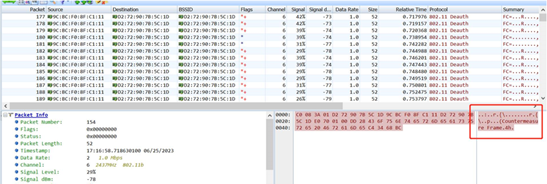
Theoretically, during the wips countermeasure process, the AP will not only spoof the terminal mac to send deauth to the hotspot, but also spoof the hotspot to send deauth to the terminal. However, the on-site AP only spoofs the terminal to send deauth to the hotspot. It is suspected that the countermeasure failed because the AP did not spoof the hotspot to send deauth messages to the terminal. After confirmation, it was found that the countermeasure message was only unidirectional after countermeasure enhance was configured. Then countermeasure enhance was deleted for testing. The air interface packet capture showed that the AP not only spoofed the terminal mac to send deauth to the hotspot, but also spoofed the hotspot to send deauth to the terminal. However, the countermeasure still did not take effect, and the terminal could still be stably connected.
Since the Apple mobile phone system version used on site is the latest version, experience shows that wips can normally counter the hotspot of previous versions of Apple mobile phones, so we asked the site to find an old version of iOS 15.6.1 mobile phone for testing, and found that the counter-effect is quite obvious. So the problem can be basically confirmed that the new version of iOS has taken some protective measures against wips counter-attack. After research, it was found that iOS16 and above versions use WPA3 encryption by default. If the client connecting to the hotspot also supports WPA3, then the management frames of the client and Apple hotspot are protected in the protocol, so the deauth message sent by wips cannot be recognized by the terminal and hotspot, because the counter-message is invalid for both the terminal and the hotspot. In addition, Android phones also have options to support wpa3 and wpa2. If wpa3 is selected, it is the same as iPhone and cannot be countered. The good counter-effect on Android on site is because the Android terminal uses WPA2 encryption to release the hotspot. The default version of iOS 15 is also wpa2, so there is no problem with wips counter-attack.
Solution
The management frames in the WPA3 encryption method are protected. In principle, the emergence of WPA3 is to prevent wireless networks from being attacked. Countermeasures are actually equivalent to an attack. If both the terminal that releases the hotspot and the terminal that connects to the hotspot use the WPA3 encryption method, it is impossible to counter the hotspot using WPA3. It is currently found that iOS 16 and above versions use the WPA3 encryption method by default, and some Android terminals can also release WPA3 hotspots.
