Network Topology
None
Problem Description
Refer to the official website 1.18.4 LDAP authentication configuration for SSH users
https://www.h3c.com/en/d_202006/1301381_294551_0.htm
Configuring the switch
# Configure IP addresses for interfaces. (Details not shown.)
# Create local RSA and DSA key pairs.
<Switch> system-view
[Switch] public-key local create rsa
[Switch] public-key local create dsa
# Enable the SSH service.
[Switch] ssh server enable
# Enable scheme authentication for user lines VTY 0 through VTY 63.
[Switch] line vty 0 63
[Switch-line-vty0-63] authentication-mode scheme
[Switch-line-vty0-63] quit
# Enable the default user role feature to assign authenticated SSH users the default user role network-operator.
[Switch] role default-role enable
# Configure an LDAP server.
[Switch] ldap server ldap1
# Specify the IP address of the LDAP authentication server.
[Switch-ldap-server-ldap1] ip 10.1.1.1
# Specify the administrator DN.
[Switch-ldap-server-ldap1] login-dn cn=administrator,cn=users,dc=ldap,dc=com
# Specify the administrator password.
[Switch-ldap-server-ldap1] login-password simple admin!123456
# Configure the base DN for user search.
[Switch-ldap-server-ldap1] search-base-dn dc=ldap,dc=com
[Switch-ldap-server-ldap1] quit
# Create an LDAP scheme.
[Switch] ldap scheme ldap-shm1
# Specify the LDAP authentication server.
[Switch-ldap-ldap-shm1] authentication-server ldap1
[Switch-ldap-ldap-shm1] quit
# Create an ISP domain named bbb and configure authentication, authorization, and accounting methods for login users.
[Switch] domain bbb
[Switch-isp-bbb] authentication login ldap-scheme ldap-shm1
[Switch-isp-bbb] authorization login none
[Switch-isp-bbb] accounting login none
[Switch-isp-bbb] quit
Verifying the configuration
# Initiate an SSH connection to the switch, and enter username aaa@bbb and password ldap!123456. The user logs in to the switch. (Details not shown.)
# Verify that the user can use the commands permitted by the network-operator user role. (Details not shown.)
The problem is insufficient login permissions after configuration.
Process Analysis
Still fails after changing to network-admin
line vty 0 63
authentication-mode scheme
user-role network-operator
Normally, you need to configure LDAP attribute mapping to implement the network-admin permissions of ying"suser-role Add a new object group.
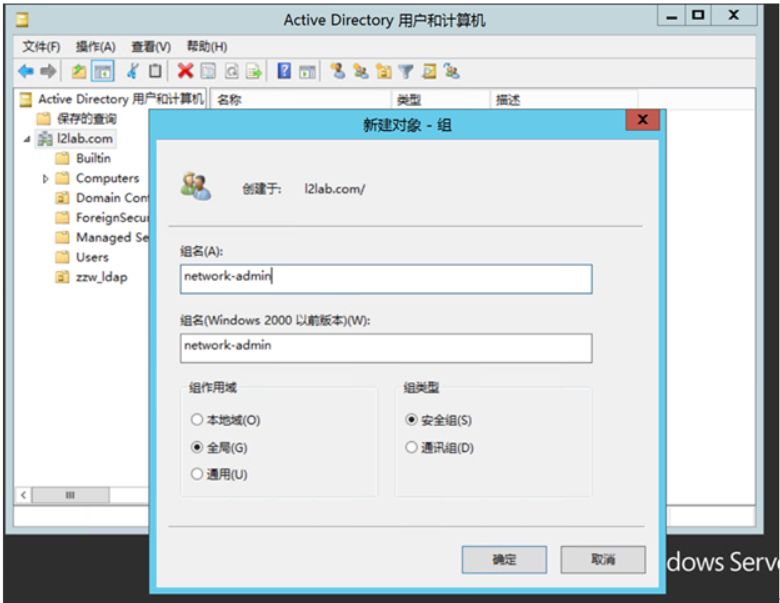
After the user is added, set the primary group to apply.
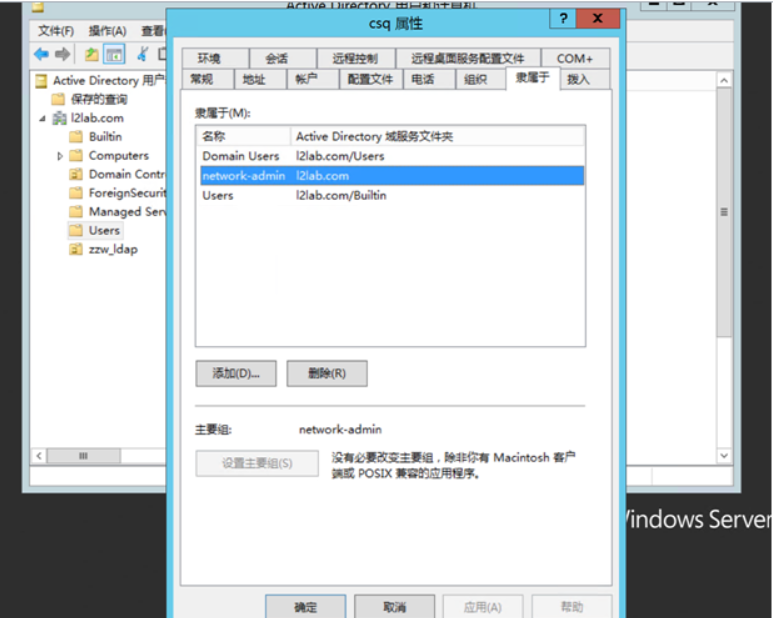
Corresponding to the configuration of the LDAP server, the device needs to be configured.
ldap attribute-map test
map ldap-attribute memberof prefix cn= delimiter , aaa-attribute user-role
However, this user-role cannot be configured. Only the following two parameters can be configured. After the test creates the user-group group, the user-role cannot be called.
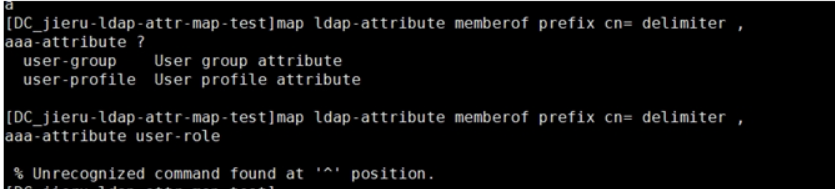
Configuring user-gourp has no effect, and the attribute map parameter is still not configured.
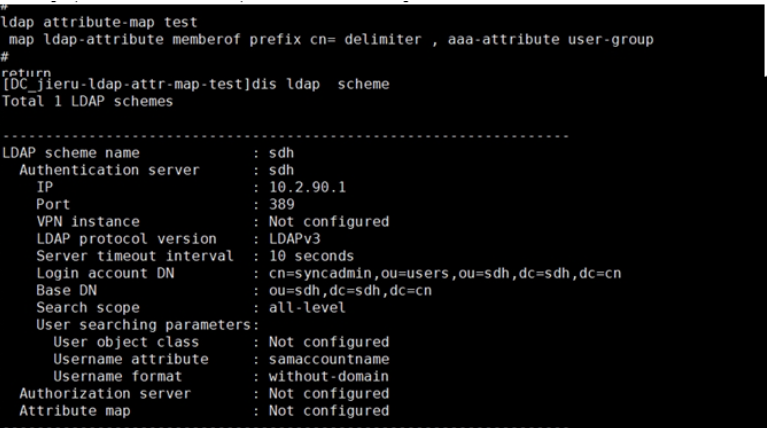
Solution
After confirmation, the current device does not support ldap authorization, and will give users the lowest level-0 permissions; and most switches do not support it.
If you want high-level permissions, you can configure it to hwtacacs or local.
[H3C-isp-aaa]authorization login ?
hwtacacs-scheme Specify HWTACACS scheme
local Specify local scheme
none Specify none scheme
radius-scheme Specify RADIUS scheme
Or you can circumvent it by: Configure super password role network-admin simple XXX, then complete ldap authentication, log in to the device and then switch the user role to network-admin permissions.
