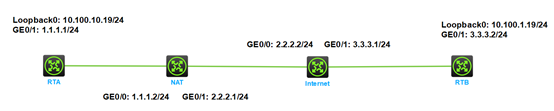
Network Topology
Topology:
Configuration Steps
Initiator configuration:
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 1.1.1.1 255.255.255.0
ipsec apply policy policy1
#
ip route-static 0.0.0.0 0 1.1.1.2
#
acl number 3102
rule 0 permit ip source 10.100.10.0 0.0.0.255 destination 10.100.1.0 0.0.0.255
#
ipsec transform-set transform1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy policy1 1 isakmp
transform-set transform1
security acl 3102
remote-address 3.3.3.2
ikev2-profile profile1
#
ikev2 keychain keychain1
peer 1
address 3.3.3.2 255.255.255.0
identity address 3.3.3.2
pre-shared-key ciphertext $c$3$MEJGUylrkdw/r9IiynSPJSon5URtCw==
#
ikev2 profile profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain keychain1
identity local fqdn RTA
match remote identity address 3.3.3.2 255.255.255.0
#
Responder configuration:
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 3.3.3.2 255.255.255.0
nat outbound
ipsec apply policy policy1
ipsec no-nat-process enable
#
ip route-static 0.0.0.0 0 3.3.3.1
#
acl advanced 3101
rule 0 permit ip source 10.100.1.0 0.0.0.255 destination 10.100.10.0 0.0.0.255
#
ipsec transform-set transform1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template template1 1
transform-set transform1
security acl 3101
ikev2-profile profile1
#
ipsec policy policy1 1 isakmp template template1
#
ikev2 keychain keychain1
peer 2
address 0.0.0.0 0.0.0.0
identity fqdn RTA
pre-shared-key ciphertext $c$3$kAOvpRjSMt0pL8YcFuOHx5PbV4nMPQ==
#
ikev2 profile profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain keychain1
match remote identity fqdn RTA
#
Key Configuration
Note that the responder uses the fqdn to identify the peer.
<RTA>dis ikev2 sa
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
1 1.1.1.1/4500 3.3.3.2/4500 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
<RTA>dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/1
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Initiator
Path MTU: 1436
Tunnel:
local address: 1.1.1.1
remote address: 3.3.3.2
Flow:
sour addr: 10.100.10.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.100.1.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3699712578 (0xdc852242)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3579
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 1928937971 (0x72f941f3)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3579
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: Y
Status: Active
<RTA>
<RTB>dis ikev2 sa
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
1 3.3.3.2/4500 2.2.2.1/1024 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
<RTB>dis ipsec sa
-------------------------------
Interface: GigabitEthernet0/1
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Responder
Path MTU: 1436
Tunnel:
local address: 3.3.3.2
remote address: 2.2.2.1
Flow:
sour addr: 10.100.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.100.10.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1928937971 (0x72f941f3)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3393
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 3699712578 (0xdc852242)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3393
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: Y
Status: Active
<RTB>
