Firewall bidirectional NAT traffic after entering IPSec scenario simulation test
- 0 Followed
- 0Collected ,1539Browsed
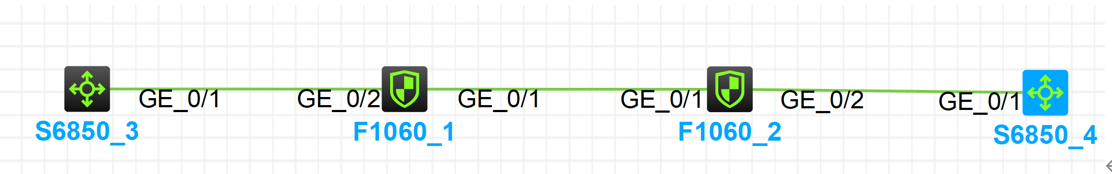
Network Topology
Experimental topology
Test background:
The customer"s firewall establishes an IPSec tunnel with a third-party firewall. Our firewall"s internal connecting device is inconvenient to configure the gateway, so we need to perform source address translation on the traffic that has undergone DNAT, changing the source address to the firewall.
Networking:
F1060_1(IPSec) GE1/0/1: 192.168.0.1
GE1/0/2: 1.1.1.1
F1060_2(IPSec/NAT) GE1/0/1: 192.168.0.2
GE1/0/2: 2.2.2.2
DNAT:192.168.1.2
Source IP after bidirectional NAT: 192.168.2.2 (Test scenario two)
S6850_3: GE1/0/1: 1.1.1.3
S6850_4: GE1/0/1: 2.2.2.4
Configuration Steps
Configuration purpose:
6850_3 accesses the DNAT-transformed address 192.168.1.2 using IP address 1.1.1.3 (Note: it can be 0.2 but here it is not 192.168.0.2). After the packet passes through F1060_2 and enters the internal network, it simultaneously converts the packet"s source and destination address, with the source being 192.168.1.2 and the destination being 2.2.2.4.
In test item two, when performing bidirectional NAT, the packet"s source address is converted to 192.168.2.2 (Note: this is not the DNAT address, but an address that does not exist on any device, requiring only the internal network users to guide the routing towards it), and the firewall will respond to ARP using the MAC address of interface GE1/0/2.
Key Configuration
Key configuration:
Match IPSec interesting traffic
acl advanced 3101, note that the source IP uses the NAT-transformed IP.
rule 0 permit ip source 2.2.2.0 0.0.0.255 destination 1.1.1.0 0.0.0.255
rule 1 permit ip source 192.168.1.2 0 destination 1.1.1.0 0.0.0.255
#
Source-ip uses the requesting device"s IP
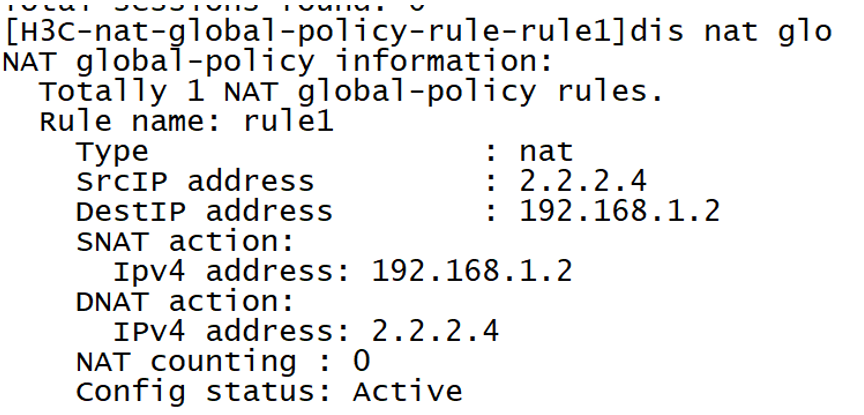
nat global-policy
rule name rule1
source-ip host 1.1.1.3 (source address before bidirectional NAT)source-ip host 1.1.1.3
destination-ip host 192.168.1.2(DNAT IP)
action snat static ip-address 192.168.1.2 (source address after bidirectional NAT)
action dnat ip-address 2.2.2.4 (real address of the server providing the service)
counting enable
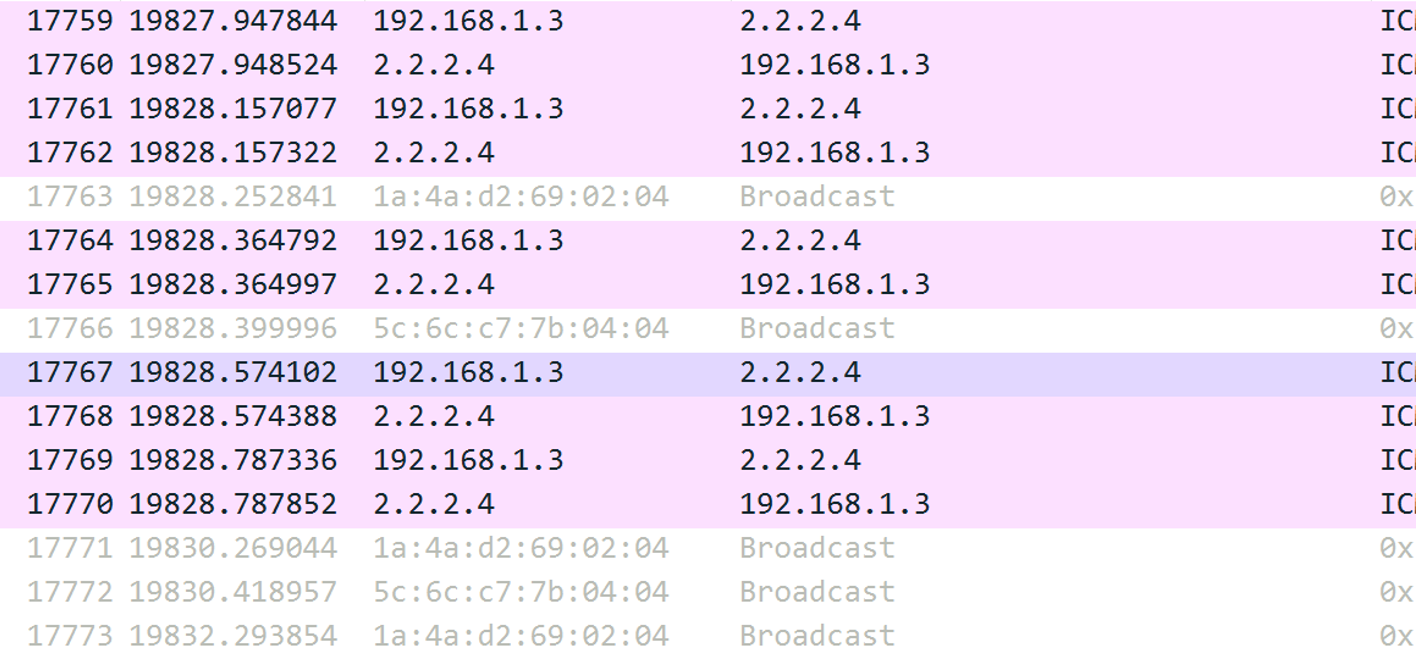
Test results:
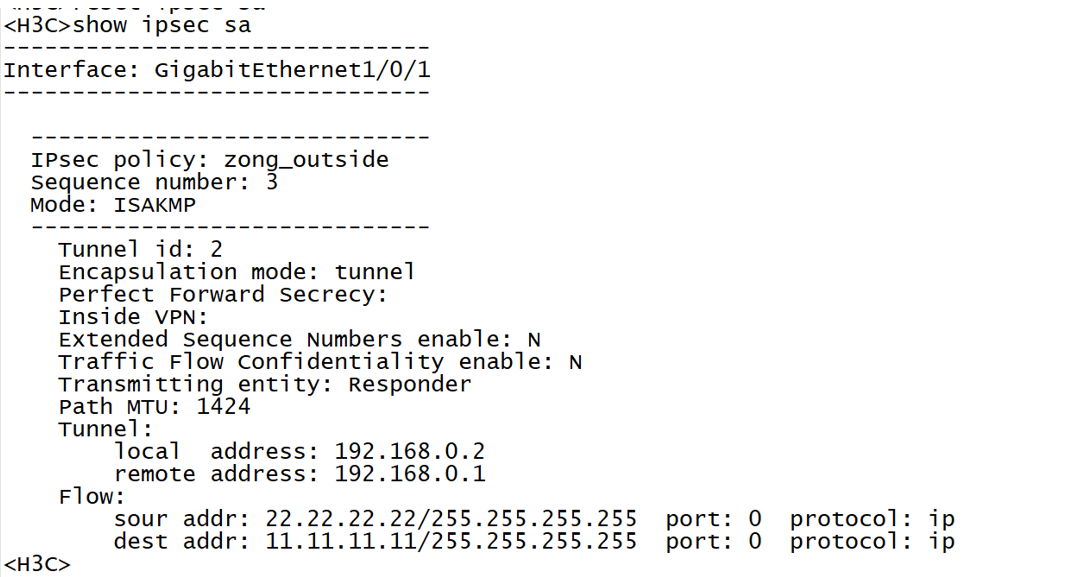
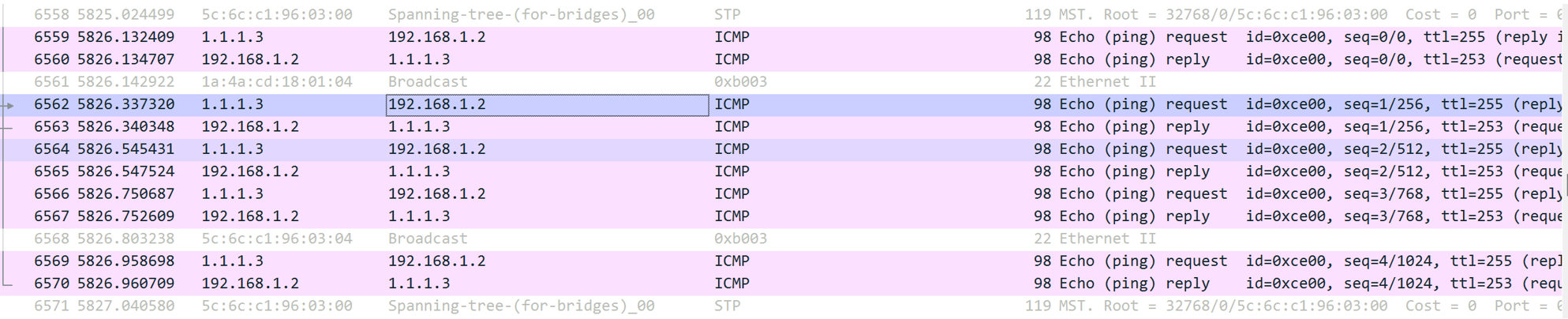
Test case two:
Source-ip uses the requesting device"s IP
nat global-policy
rule name rule1
source-ip host 1.1.1.3 (source address before bidirectional NAT)source-ip host 1.1.1.3
destination-ip host 192.168.1.2(DNAT IP)
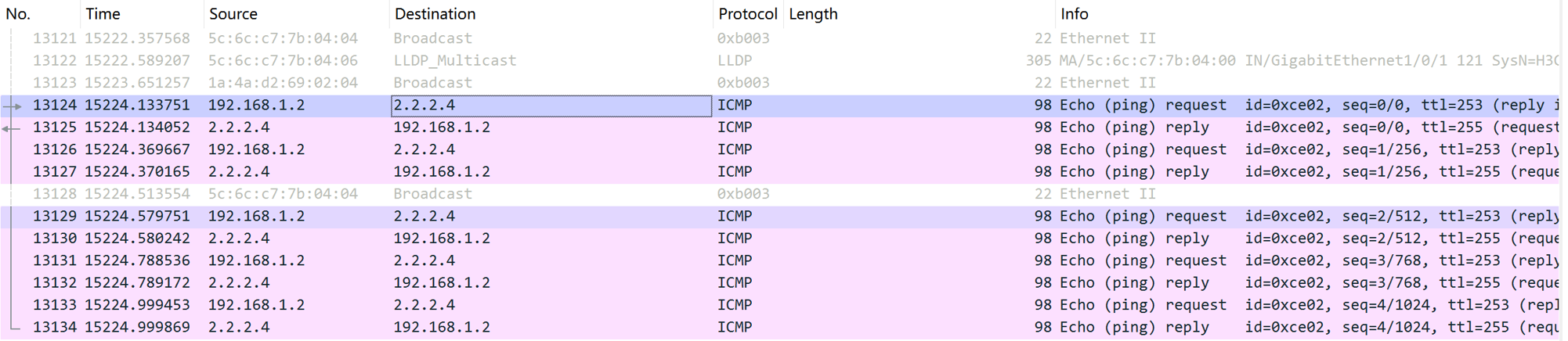
action snat static ip-address 192.168.2.2 (source address after bidirectional NAT)
action dnat ip-address 2.2.2.4 (real address of the server providing the service)
counting enable
Actual results