Abnormal number of gateway ping reply packets in VRRP networking based on M-LAG at a certain site S10506X-G
- 0 Followed
- 0Collected ,386Browsed
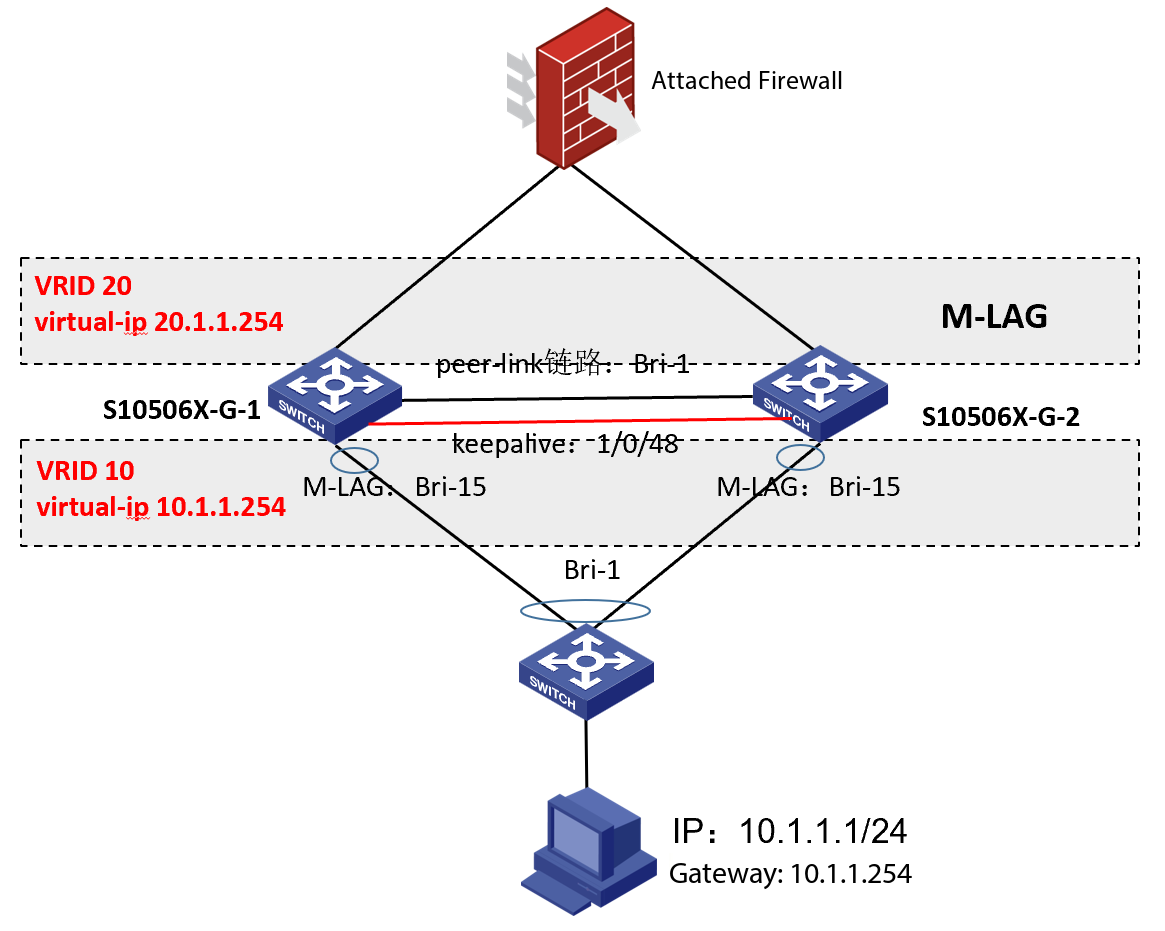
Network Topology
The customer network setup is as follows: S10506X-G serves as an M-LAG VRRP active-active gateway. The test terminal's gateway is on the M-LAG, and the VRRP-related int-vlan interface is bound to PBR to divert some traffic to the bypass firewall.(Information has been desensitized; the following network setup and IP addresses are unrelated to the actual customer environment)
Problem Description
The terminal (10.1.1.1) pinged the VRRP virtual address of the gateway (10.1.1.254) and found that the number of ping replies was significantly higher than the number of requests, and there were many hops when tracert the gateway address.
The main configuration of the M-LAG device is as follows:
#
interface Vlan-interface10
ip address 10.1.1.252 255.255.255.0
vrrp vrid 10 virtual-ip 10.1.1.254
ip policy-based-route PBR
#
policy-based-route PBR permit node 10
if-match acl 3000
apply next-hop 20.1.1.1
#
#
acl number 3000
rule 0 permit ip source 30.1.1.0 0.0.0.255
rule 5 permit ip source 10.1.1.0 0.0.0.255
#
#
interface Bridge-Aggregation15
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 10
link-aggregation mode dynamic
port m-lag group 15
#
Process Analysis
1. In theory, traffic pinging the gateway should not match PBR to the firewall, and simulator tests show no such phenomenon. However, packet capture on the firewall confirms that packets from terminal pings to the gateway are indeed received.
2. It is acknowledged that the current device (S10506X-G Version 7.1.070, Release 7755P03) operates this way: PBR can match ping packets destined for itself, sending one copy locally and another via PBR. That is, even ping packets destined for the local device will be forwarded once by PBR.
Solution
Add a node on PBR to match traffic pinging the local machine and execute no action for mitigation.
For example
policy-based-route PBR permit node 1
if-match acl 3010
policy-based-route PBR permit node 10
if-match acl 3000
apply next-hop 20.1.1.1
acl num 3010
rule permit ip 10.1.1.254 0 matches packets pinging the local machine
