Technical Announcement on the Impact of the 2025.8.19 Expiration of EIA Built-in Certificates and Countermeasures
- 0 Followed
- 0Collected ,3463Browsed
Product Model
|
Announcement category |
Mandatory Immediate Rectification |
|
Operational requirements |
Patch upgrade |
I.
(1) AD-Campus EIA
(2) iMC EIA
(3) iMC SDNAPP EIA
Involved Version
All versions
Problem Description
The original server certificate built in EIA will expire on August 19, 2025. After the certificate expires, the certificate authentication business using the built-in certificate will be affected.
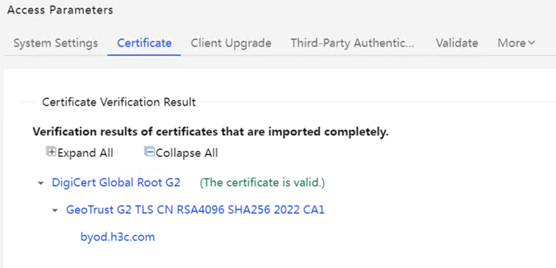
The method to confirm whether the site uses the H3C built-in certificate is as follows:
Enter the product certificate configuration page to check whether the certificate expiration time is 2025-08-19 and whether the subject is CN=byod.h3c.com,O=新华三技术有限公司,L=杭州市,ST=浙江省,C=CN.
(1) iMC EIA view screenshot:
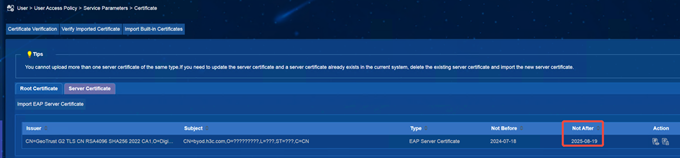
(2) AD-Campus EIA view screenshot. The menu location varies between versions and is subject to the on-site environment:
If the subject and expiration time are as shown in the figure above, it means that the customer uses the H3C built-in certificate.
Cause Analysis
The built-in certificate validity period expires.
Workaround/Solutions
The above problems can be solved by importing a new certificate. For the new certificate, refer to ‘EIA Certificate (Date of expiry 22-8-2026)’. The certificate import operation method is as follows:
1. Delete the original old root certificate
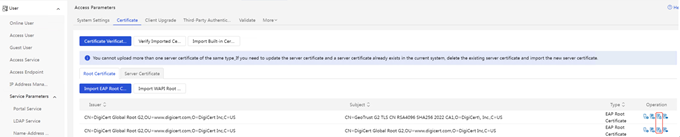
(1) iMC EIA: Enter [User] | [Access Policy Management] | [Service Parameter Configuration] | [Certificate] interface, select [Root Certificate], and delete the old certificate.
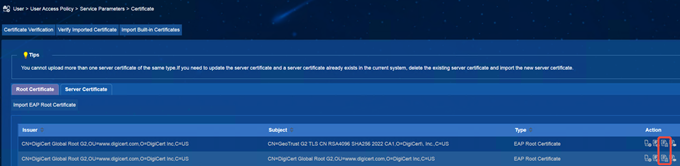
(2) AD-Campus EIA: Select [Root Certificate], and delete the original old certificate. The menu locations of different versions are different and are subject to the on-site environment.
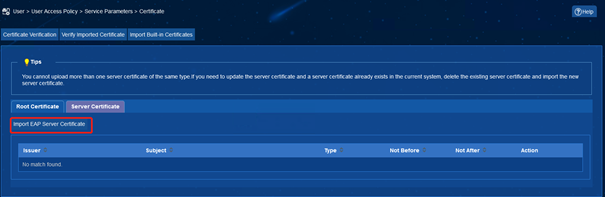
2. Delete the original old server certificate
(1) iMC EIA: Enter [User] | [Access Policy] | [Service Parameter] | [Certificate] interface, select [Server Certificate], and delete the old certificate.
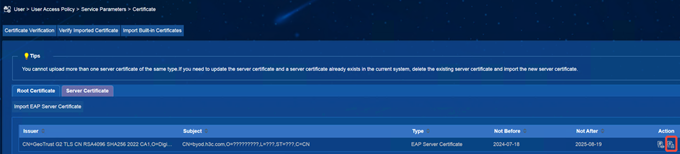
(2)
3. Import the new root certificate
(1) iMC EIA: Enter [User] | [User Access Policy] | [Service Parameter] | [Certificate] interface, select [Root Certificate], and import topRoot.cer and secondRoot.cer in turn. (Note: The following screenshot takes importing topRoot.cer as an example, and topRoot.cer, secondRoot.cer is operated in the same way)
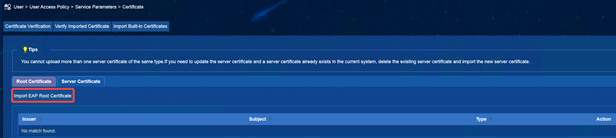
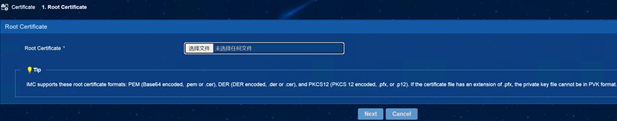
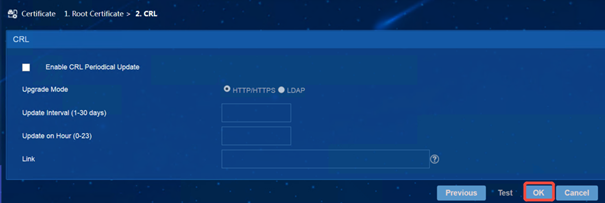
(2)
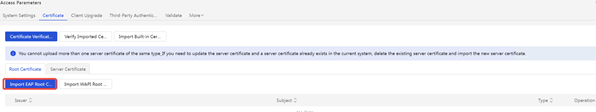
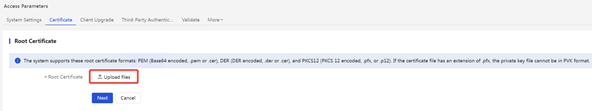
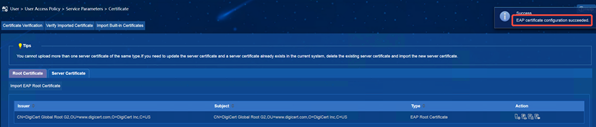
4. Import the new version of the server certificate
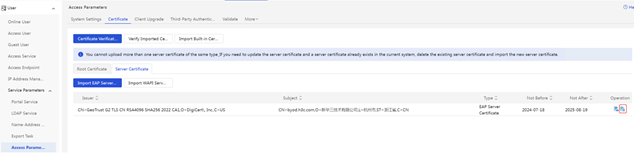
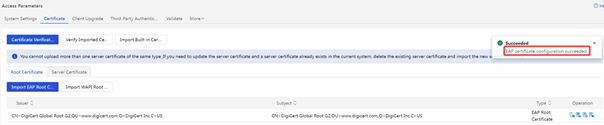
(1) iMC EIA: Enter [User] | [Access Policy] | [Service Parameter] | [Certificate] interface, select [Server Certificate], and import the server certificate file server.crt and the server certificate private key file server.key, and the password is empty.
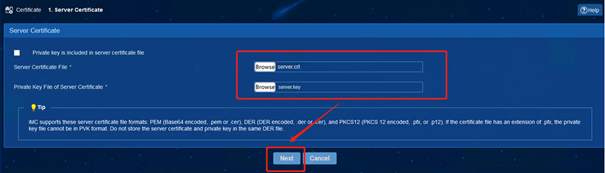
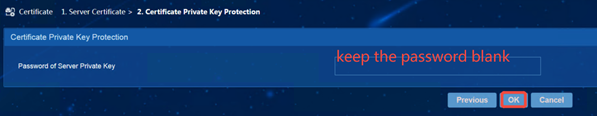
(2) AD-Campus EIA: Select [Server Certificate], and import the server certificate file server.crt and the server certificate private key file server.key, and the password is empty.
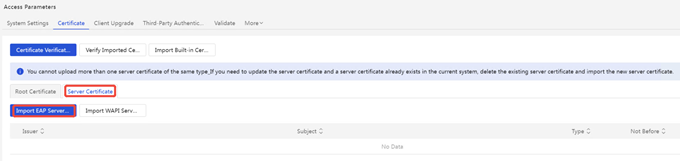
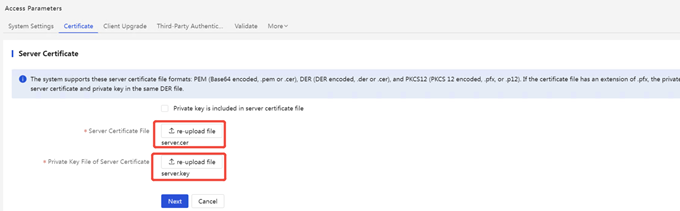
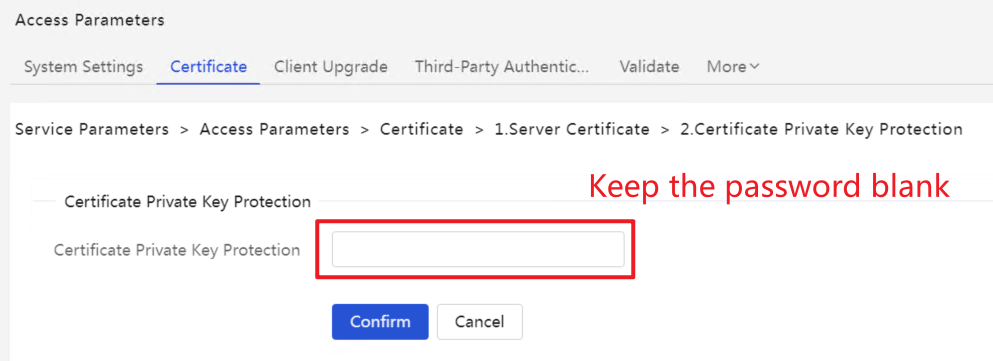
5. Verify after the new version of the certificate is imported successfully
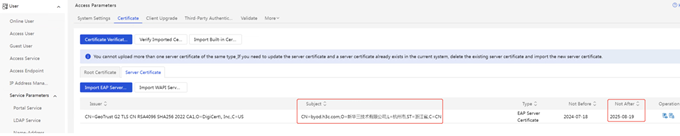
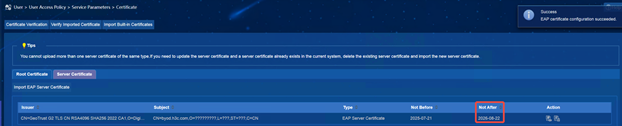
After the certificate is imported successfully, you can see on the page that the validity period of the certificate has changed to "2026-08-22".
(1) iMC EIA page display:
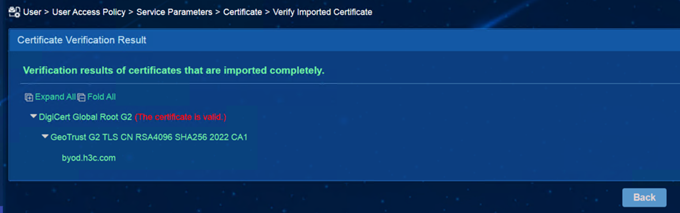
Click [Verify Imported Certificate] to prompt that the certificate is valid:
(2) AD-Campus EIA page displays:
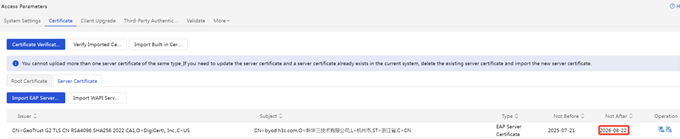
Click [Verify Imported Certificate] to prompt that the certificate is valid: