Connectivity Issue in IKEv2 IPsec Tunnel with FortiGate Firewall
- 0 Followed
- 0Collected ,3770Browsed
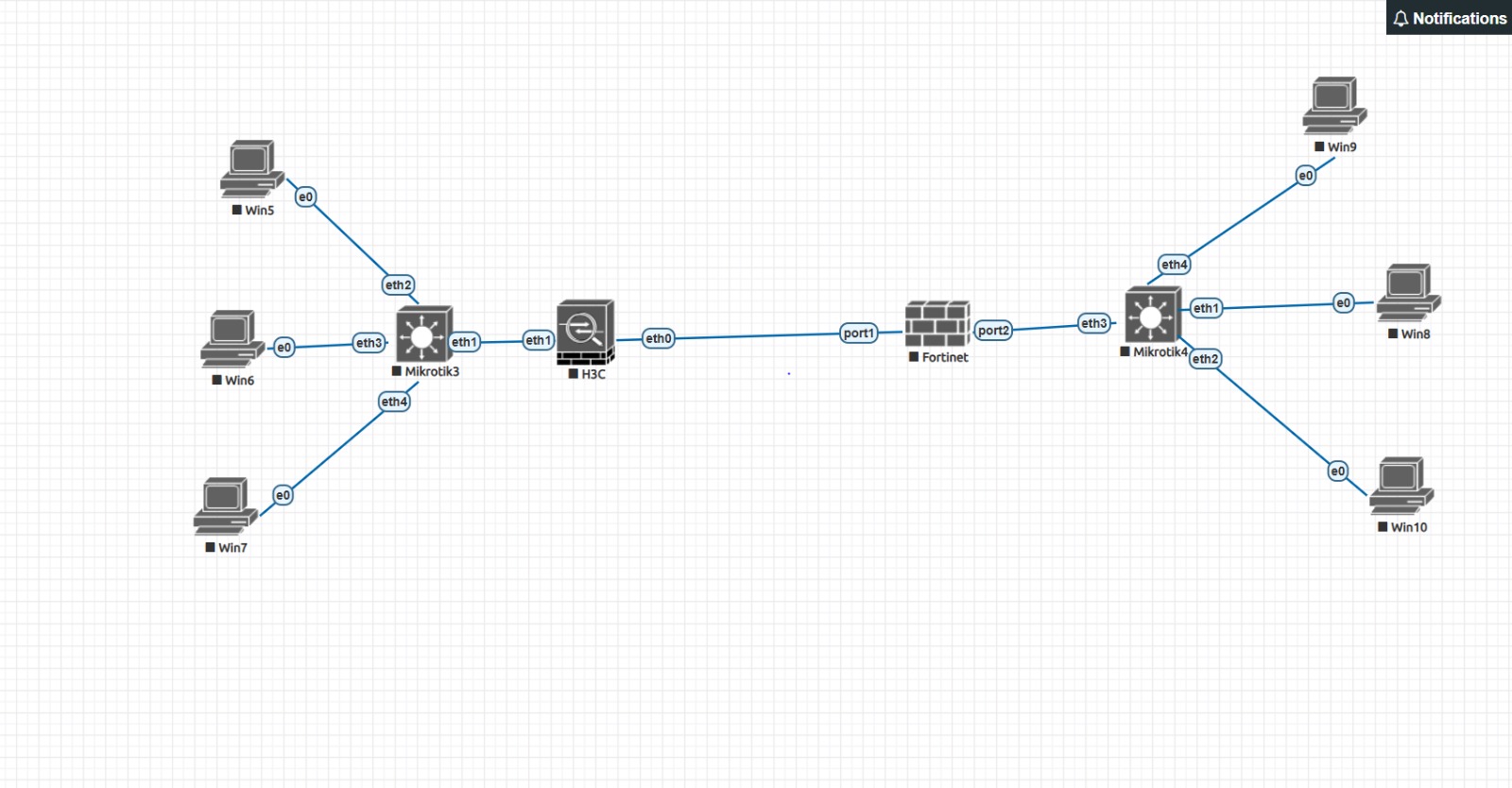
Network Topology
Topology
Problem Description
Problem Description
The customer’s H3C SecPath F5000 has an IPsec VPN configured to a FortiGate firewall. Although both IKE phases (Phase-1 and Phase-2) are negotiated successfully, hosts on the local LAN cannot reach hosts on the remote LAN. Packet captures show outbound traffic leaving the H3C and reaching the FortiGate, but replies from the FortiGate are not received back at the H3C ,
Process Analysis
IKE Phase-1 and Phase-2: UP
Traffic capture on H3C: outbound packets reach FortiGate; responses not observed.
Intermittent single-packet replies seen occasionally, otherwise zero replies.
Troubleshooting
Problem Root Cause
In general, more recent IPsec VPN encryption and authentication algorithms may not be supported by older NP processors. For example, NP4 network processors do not support SHA-256, SHA-384, and SHA-512. IPsec traffic with unsupported algorithms is not offloaded and instead is processed by the FortiGate CPU. In addition, this configuration may cause packet loss and other performance issues. If you experience packet loss or performance problems you should set the npu-offload option to disable. Future FortiOS versions should prevent selecting algorithms not supported by the hardware.
Solution
The issue was traced to the NPU offload feature on the FortiGate. After disabling NPU offload, the traffic passed through the IPsec tunnel normally, and LAN-to-LAN communication was restored.
Use the following command to disable NP offloading for an interface-based IPsec VPN phase 1:
config vpn ipsec phase1-interface
edit phase-1-name
set npu-offload disable
end
Use the following command to disable NP offloading for a policy-based IPsec VPN phase 1:
config vpn ipsec phase1
edit phase-1-name
set npu-offload disable
end
The npu-offload option is enabled by default.
